A researcher has launched a software to bypass Google’s new App-Certain encryption cookie theft defenses and extract saved credentials from the Chrome net browser.
The software, referred to as ‘Chrome-App-Certain-Encryption-Decryption’, was launched by cybersecurity researcher Alexander Hagenah after he seen that others have been already discovering related bypasses.
Though the software accomplishes what a number of information theft operations have already added to their malware, its public availability will increase the chance for Chrome customers who proceed to retailer delicate information of their browsers.
Encryption issues linked to Google functions
Google launched App-Certain encryption in July (Chrome 127) as a brand new safety mechanism that encrypts cookies utilizing a Home windows service operating with SYSTEM privileges.
The aim was to guard delicate data from data-stealing malware, which runs with the permissions of the logged-in consumer, making it unimaginable to decrypt stolen cookies with out first gaining SYSTEM privileges and probably elevating alarms in safety software program. .
“As a result of the App-Certain service runs with system privileges, attackers should do greater than merely persuade a consumer to run a malicious software.” google defined in July.
“Now, malware has to achieve system privileges or inject code into Chrome, one thing reputable software program should not do.”
Nevertheless, by September, a number of data thieves had discovered methods to bypass new safety characteristic and supply their cybercriminal purchasers with the power to re-steal and decrypt delicate data from Google Chrome.
Google advised BleepingComputer then that the “cat and mouse” sport between data-stealing builders and their engineers was at all times anticipated and that they by no means assumed their protection mechanisms can be bulletproof.
As an alternative, with the introduction of App-Certain encryption, they hoped to lastly lay the muse to step by step construct a extra sturdy system. Beneath is Google’s response at the moment:
“We’re conscious of the disruption this new protection has brought about to the information theft panorama and, as we famous within the weblog, we hope that this safety will trigger a change in attacker conduct in direction of extra observable strategies similar to injection or scraping from reminiscence. This matches the brand new conduct we’ve seen.
“We proceed to work with working system and antivirus distributors to attempt to extra reliably detect these new sorts of assaults, in addition to proceed to strengthen defenses to enhance safety towards information thieves for our customers.” – A Google spokesperson
Bypass now publicly obtainable
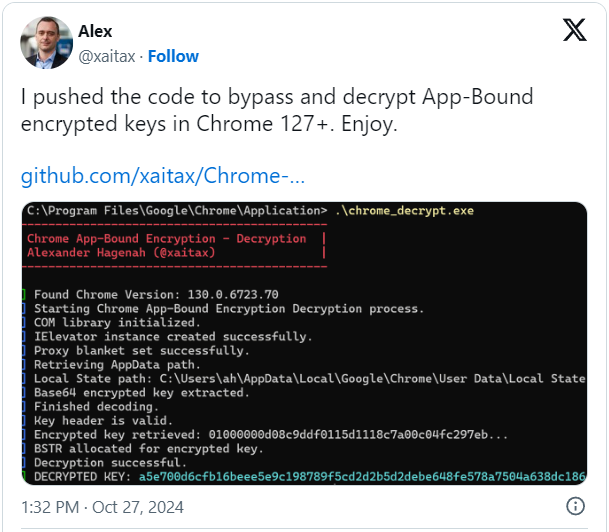
Yesterday, Hagenah made its App-Certain encryption bypass software obtainable on GitHubsharing supply code that permits anybody to be taught and compile the software.
“This software decrypts app-bound encrypted keys saved in Chrome’s native state file, utilizing Chrome’s inner COM-based IElevator service.” learn the undertaking description.
“The software offers a option to recuperate and decrypt these keys, which Chrome protects utilizing App-Certain Encryption (ABE) to stop unauthorized entry to safe information like cookies (and probably passwords and cost data sooner or later).”
To make use of the software, customers want to repeat the executable to the Google Chrome listing which is often situated at C:Program FilesGoogleChromeApplication. This folder is protected, so customers should first receive administrator privileges to repeat the executable to that folder.
Nevertheless, that is often simple to realize since many Home windows customers, particularly customers, use accounts which have administrative privileges.
When it comes to its precise affect on Chrome’s safety, the researcher g0njxa advised BleepingComputer that Hagenah’s software demonstrates a primary methodology that the majority information thieves have now surpassed to steal cookies from all variations of Google Chrome.
Toyota Malware Analyst russian panda He additionally confirmed to BleepingComputer that Hagenah’s methodology resembles the early circumvention approaches that information thieves took when Google first carried out App-Certain encryption in Chrome.
“Lumma used this methodology: instantiating the Chrome IElevator interface by way of COM to entry the Chrome Elevation Service to decrypt cookies, however this may be fairly noisy and straightforward to detect,” Russian Panda advised BleepingComputer.
“They’re now utilizing oblique decryption with out straight interacting with Chrome’s Elevation service.”
Nevertheless, g0njxa commented that Google nonetheless hasn’t caught up, so consumer secrets and techniques saved in Chrome might be simply stolen utilizing the brand new software.
In response to the discharge of this software, Google shared the next assertion with BleepingComputer:
“This (xaitax’s) code requires administrator privileges, demonstrating that we’ve efficiently raised the quantity of entry wanted to efficiently carry out this kind of assault,” Google advised BleepingComputer.
Whereas it’s true that administrator privileges are required, it doesn’t seem to have affected information-stealing malware operations, which have solely elevated within the final six months and goal customers by way of zero-day vulnerabilities, faux fixes to GitHub pointsand even solutions on StackOverflow.