QNAP has launched safety patches for a second zero-day bug exploited by safety researchers throughout final week’s Pwn2Own hacking contest.
This important SQL injection (SQLi) vulnerability, tracked as CVE-2024-50387was present in QNAP SMB service and is now fastened in variations 4.15.002 or later and h4.15.002 and later.
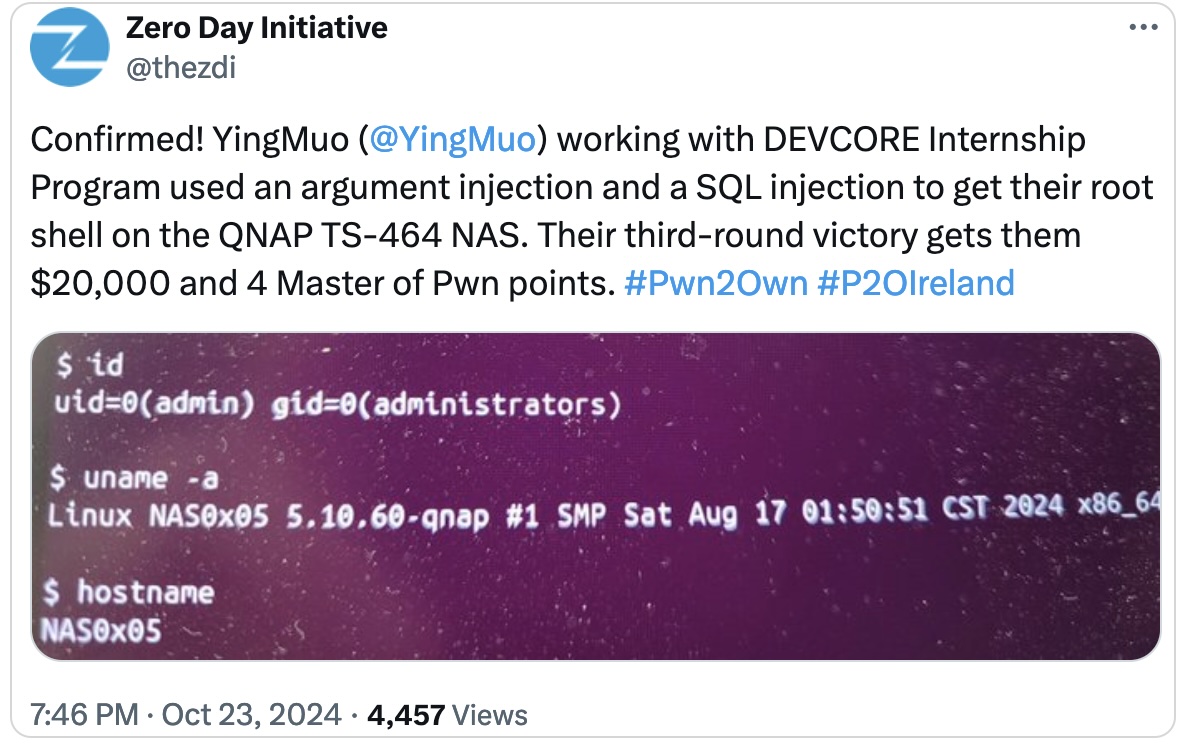
The zero-day bug was fastened per week after permitting YingMuo (who works with the DEVCORE internship program) to get a root shell and take cost of a QNAP TS-464 NAS machine at Pwn2Own Eire 2024.
On Tuesday, the corporate organized One other zero day in your HBS 3 Hybrid Backup Sync Information backup and catastrophe restoration answer, exploited by the Viettel Cyber Safety crew at Pwn2Own to execute arbitrary instructions and hack a TS-464 NAS machine.
Group Viettel received Pwn2Own Eire 2024 after 4 days of competitors, throughout which greater than $1 million in prizes had been awarded to hackers who demonstrated 70+ distinctive zero-day vulnerabilities.
Whereas QNAP patched each vulnerabilities inside per week, distributors sometimes take their time releasing safety patches after the Pwn2Own contest, provided that they’ve 90 days till Pattern Micro’s Zero Day Initiative releases particulars in regards to the bugs revealed through the contest. .
To replace the software program in your NAS machine, log in to QuTS hero or QTS as an administrator, go to Software Middle, seek for “SMB Service” and click on “Replace”. This button is not going to be accessible if the software program is already up to date.
Fast patching is extremely beneficial as QNAP units are fashionable targets for cybercriminals as a result of they’re generally used to backup and retailer delicate private information. This makes them straightforward targets for putting in information-stealing malware and the proper leverage to power victims to pay a ransom to recuperate their information.
For instance, in June 2020, QNAP warned about eCh0raix ransomware assaultswhich exploited vulnerabilities within the Photograph Station app to hack and encrypt QNAP NAS units.
QNAP additionally alerted its prospects in September 2020 in regards to the AgeLocker ransomware assaults focusing on publicly uncovered NAS units working previous and weak variations of Photograph Station. In June 2021, eCh0raix (QNAPCrypt) returned with new assaults exploiting identified vulnerabilities and brute-forcing NAS accounts utilizing weak passwords.
Different current assaults focusing on QNAP units embody useless bolt, Mateand eCh0raix ransomware campaigns, which abused a number of safety vulnerabilities to encrypt information on NAS units uncovered to the Web.