After getting used within the Akira and Fog ransomware assaults, a crucial Veeam Backup & Replication (VBR) safety flaw was additionally lately exploited to deploy the Frag ransomware.
Florian Hauser, safety researcher at Code White discovered That the vulnerability (tracked as CVE-2024-40711) is attributable to a deserialization of untrusted information weak point that unauthenticated menace actors can exploit to acquire distant code execution (RCE) on Veeam VBR servers.
watchtower laboratories, who printed a technical evaluation on CVE-2024-40711 September 9, delayed Launch of a proof-of-concept exploit. till September 15 to present directors sufficient time to use safety updates aired by Veeam on September 4.
Code white too delayed sharing extra particulars when it revealed the flaw as a result of “ransomware gangs might immediately abuse it.”
These delays have been induced as a result of Veeam’s VBR software program is a well-liked goal for menace actors on the lookout for fast entry to an organization’s backup information, as many corporations use it as an information safety and catastrophe restoration answer. to backup, restore and replicate digital, bodily and cloud information. machines.
Nevertheless, Sophos X-Ops incident response groups discovered which this did little or no to delay akira and Fog ransomware assaults. Risk actors exploited the RCE flaw together with stolen VPN gateway credentials so as to add fraudulent accounts to native administrator and distant desktop consumer teams on unpatched, Web-exposed servers.
Extra lately, Sophos additionally found that the identical menace exercise group (tracked as “STAC 5881”) used CVE-2024-40711 exploits in assaults that led to Frag ransomware is being deployed in compromised networks.
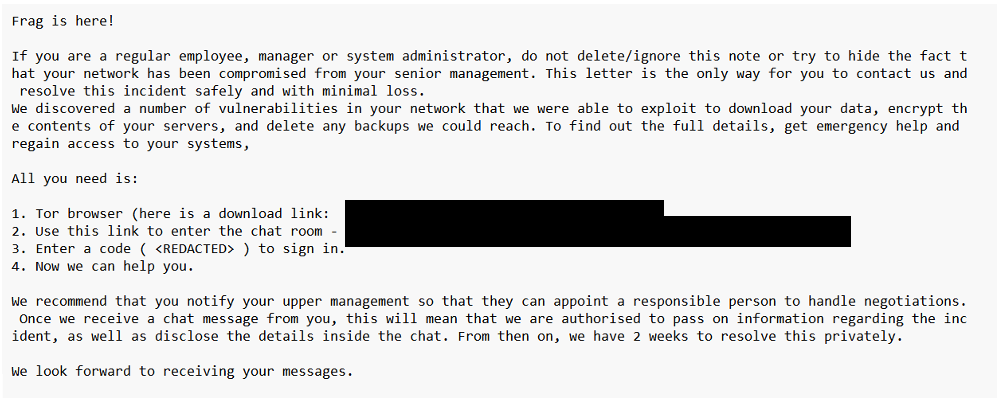
“In a latest case, MDR analysts as soon as once more noticed the ways related to STAC 5881, however this time they noticed the deployment of a beforehand undocumented ransomware known as ‘Frag.'” saying Sean Gallagher, Principal Risk Researcher at Sophos X-Ops.
“Just like earlier occasions, the menace actor used a compromised VPN machine to achieve entry, exploited the VEEAM vulnerability and created a brand new account named ‘level’. Nevertheless, on this incident an account ‘point2’ was additionally created” .
in a latest reportBritish cybersecurity agency Agger Labs mentioned the lately found Frag ransomware gang broadly makes use of Residing Off The Land binaries (LOLBins) of their assaults (professional software program already obtainable on compromised programs), making it tough for defenders to detect their exercise.
Additionally they have the same playbook to the Akira and Fog operators, as they are going to possible assault unpatched vulnerabilities and misconfigurations in backup and storage options throughout their assaults.
In March 2023, Veeam patched one other excessive severity VBR vulnerability (CVE-2023-27532) which can enable malicious actors to breach supporting infrastructure. Months later, a CVE-2023-27532 exploit (utilized in assaults linked to FIN7 menace group with monetary motivation) was deployed in ransomware assaults in Cuba focusing on US crucial infrastructure organizations.
Veeam says greater than 550,000 purchasers Its merchandise are used worldwide, together with roughly 74% of all International 2000 corporations.

