Risk actors are more and more utilizing scalable vector graphics (SVG) attachments to show phishing kinds or deploy malware whereas evading detection.
Most photographs on the internet are JPG or PNG recordsdata, that are manufactured from grids of small squares known as pixels. Every pixel has a particular coloration worth and collectively, these pixels make up the whole picture.
SVG, or scalable vector graphics, shows photographs otherwise, as a result of as a substitute of utilizing pixels, photographs are created via traces, shapes, and textual content described in textual mathematical formulation in code.
For instance, the next textual content will create a rectangle, a circle, a hyperlink, and a few textual content:
When opened in a browser, the file will generate the graphics described within the textual content above.

Supply: BleepingComputer
Since these are vector photographs, they resize robotically with out dropping picture high quality or form, making them preferrred to be used in browser functions that will have totally different resolutions.
Use SVG attachments to evade detection
The usage of SVG attachments in phishing campaigns is nothing new; BleepingComputer reported on its use in earlier points. Qbot malware campaigns and as a means of disguise malicious scripts.
Nonetheless, menace actors are more and more utilizing SVG recordsdata of their phishing campaigns, in accordance with a safety researcher. MalwareHunterTeamwho shared latest samples (1, 2) with BleepingComputer.
These examples, and others seen by BleepingComputer, illustrate how versatile SVG attachments could be, as they not solely help you show graphics however may also be used to show HTML, utilizing the
This enables menace actors to create SVG attachments that not solely show photographs but additionally create phishing kinds to steal credentials.
As proven beneath, a latest SVG attachment (VirusTotal) shows a faux Excel spreadsheet with an embedded login type that, when submitted, sends the info to the menace actors.
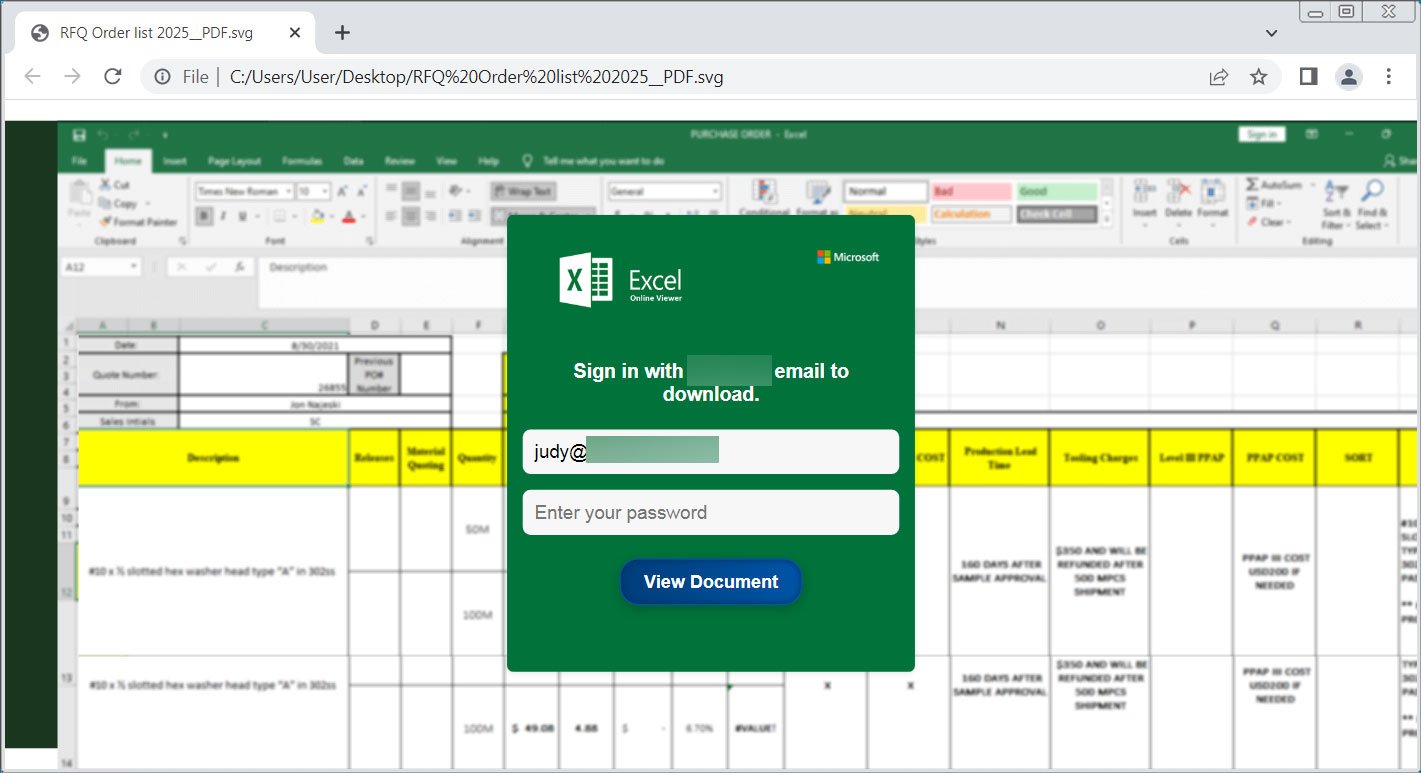
Supply: BleepingComputer
Different SVG attachments utilized in a latest marketing campaign (VirusTotal) purport to be official paperwork or requests for extra data, asking you to click on the obtain button, which then downloads malware from a distant web site.
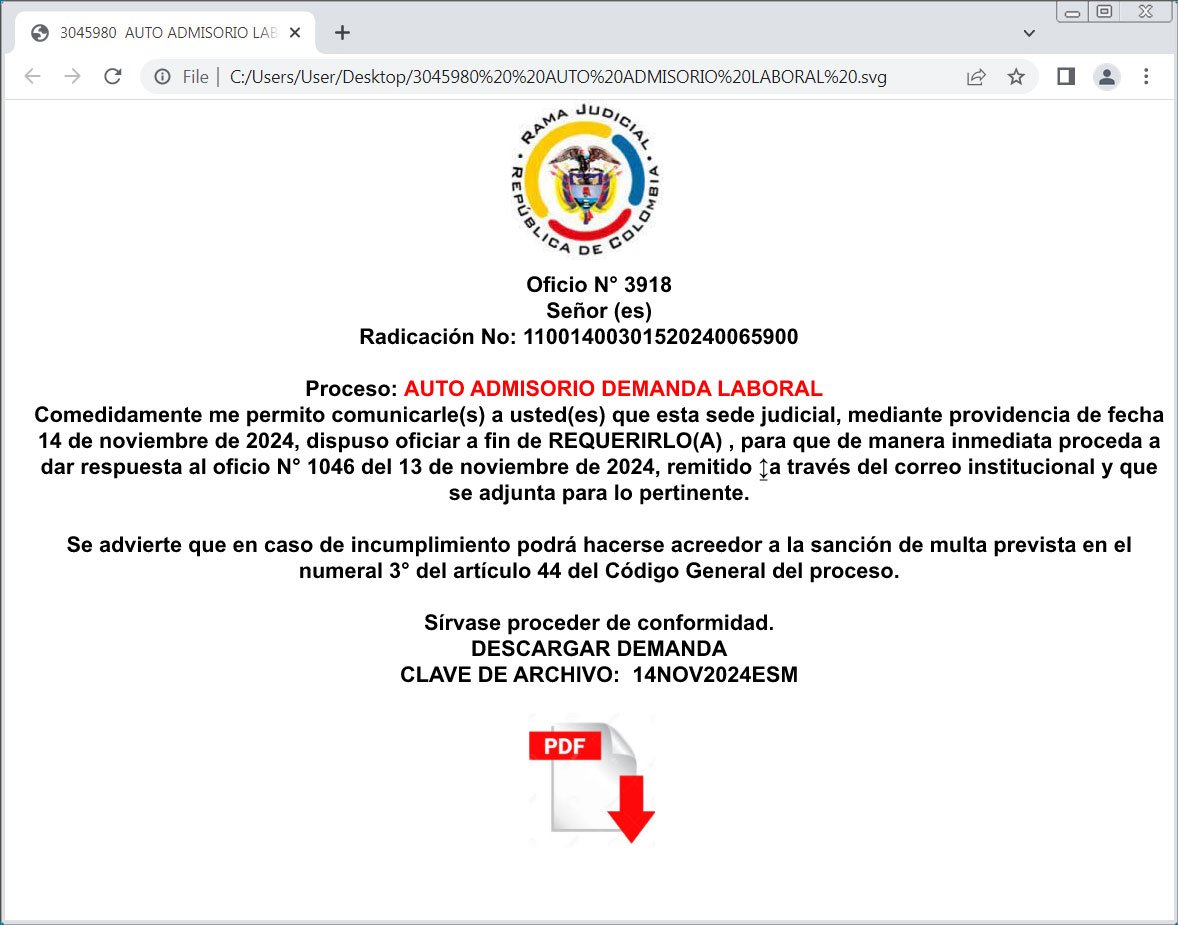
Supply: BleepingComputer
Different campaigns use SVG attachments and embedded JavaScript to robotically redirect browsers to websites internet hosting phishing kinds when the picture is opened.
The issue is that since these recordsdata are principally simply textual representations of photographs, they aren’t detected as usually by safety software program. Of the samples seen by BleepingComputer and uploaded to VirusTotal, at most, they’ve one or two detections by the safety software program.
That mentioned, receiving an SVG attachment is just not widespread in official emails and must be handled with suspicion instantly.
Except you’re a developer and anticipate to obtain all these attachments, it’s safer to delete any e-mail that incorporates them.

