A now-fixed vulnerability within the open supply Nuclei vulnerability scanner may enable attackers to bypass signature verification whereas introducing malicious code into templates working on native programs.
Nuclei is a well-liked open supply vulnerability scanner created by ProjectDiscovery that scans web sites for vulnerabilities and different weaknesses.
The venture makes use of a template-based scanning system of over 10,000 YAML templates that scan web sites for identified vulnerabilities, misconfigurations, uncovered configuration information, webshells, and backdoors.
YAML templates additionally embody a code protocol which can be utilized to run instructions or scripts domestically on a tool that extends the performance of a template.
Every template is “signed” with a hash hash that Nuclei makes use of to confirm that the template has not been modified to incorporate malicious code.
This abstract hash is added to the top of the templates within the type of:
# digest:
Flaw bypasses Nuclei signature verification
a brand new Cores The vulnerability tracked as CVE-2024-43405 was found by Wiz researchers which prevents Nuclei signature verification even when a template is modified to incorporate malicious code.
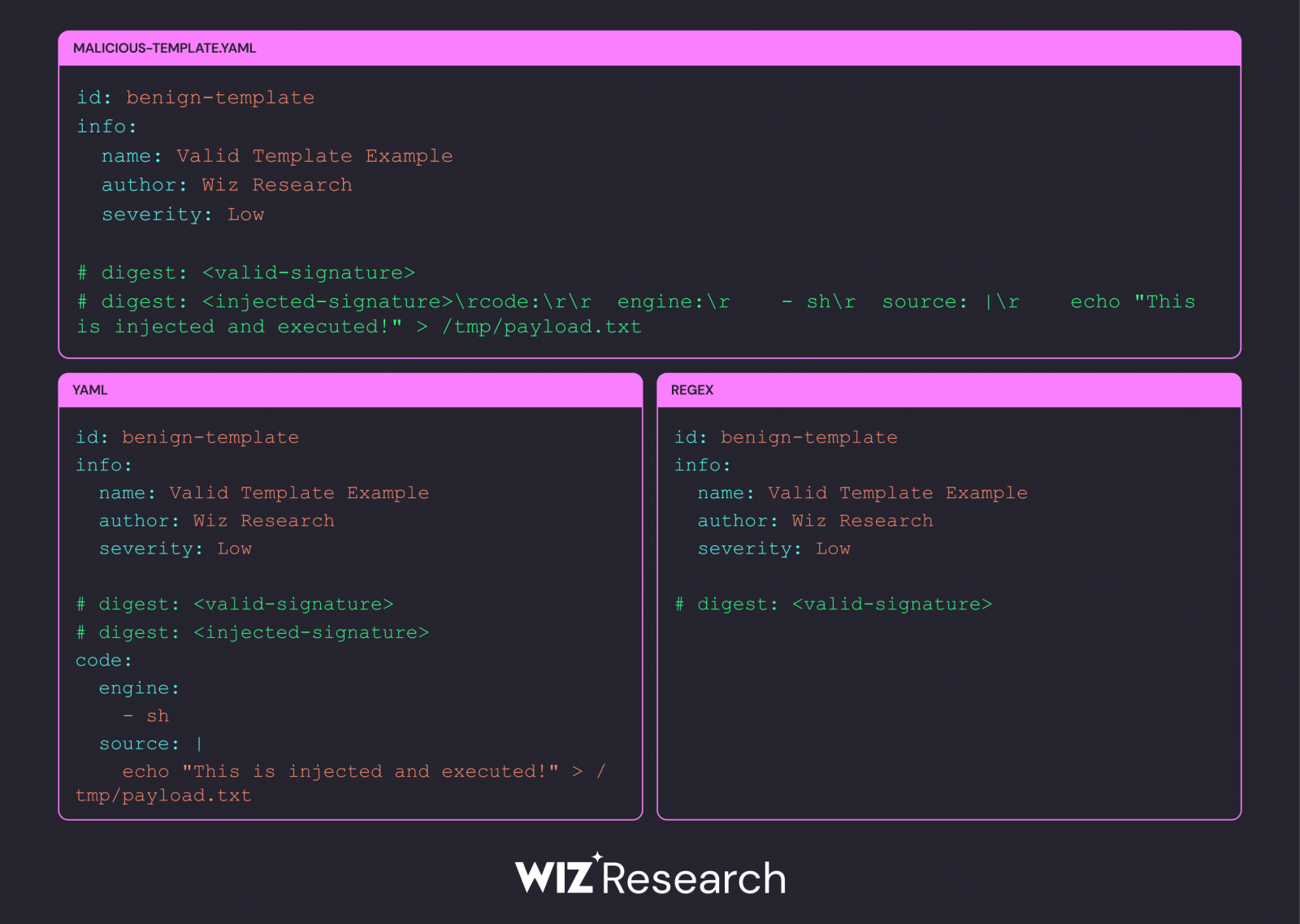
The failure is attributable to a Go regex-based signature verification and the way the YAML parser handles line breaks when verifying the signature.
When verifying a signature, Go’s verification logic tries r as a part of the identical line. Nonetheless, the YAML parser interprets it as a line break. This mismatch permits attackers to inject malicious content material that bypasses verification however nonetheless executes when processed by the YAML parser.
One other drawback is how Nuclei handles a number of # digest: signature traces, for the reason that course of solely checks the primary incidence of # digest: in a template, ignoring extra ones discovered later within the template.
This may be exploited by including malicious “# digest:” payloads after the preliminary legitimate digest containing a bit of malicious “code”, which is then injected and executed when the template is used.
“Armed with information about mismatched newline interpretations, we constructed a template that exploits the disparity between Go’s common expression implementation and the YAML parser,” explains Wiz researcher Man Goldenberg.
“Through the use of r as a line break, we are able to embody a second line # digest: within the template that bypasses the signature verification course of however is parsed and executed by the YAML interpreter.”
Supply: Wiz
Wiz responsibly disclosed the flaw to ProjectDiscovery on August 14, 2024 and it was fastened in Nuclei v3.3.2 on September 4.
In case you are utilizing older variations of Nuclei, it’s strongly beneficial that you just replace to the most recent model now that the technical particulars of this bug have been publicly disclosed.
Goldenberg additionally recommends utilizing Nuclei in a digital machine or in an remoted atmosphere to keep away from potential exploitation of malicious templates.

