Risk actors can exploit a not too long ago disclosed vulnerability within the open supply Frequent Unix Printing System (CUPS) to launch distributed denial of service (DDoS) assaults with a 600x amplification issue.
As Akamai safety researchers found, a safety flaw CVE-2024-47176 within the cups-browsed daemon that may be chained with three different bugs to acquire distant code execution on Unix-like techniques through a single UDP packet can be leveraged to amplify DDoS assaults.
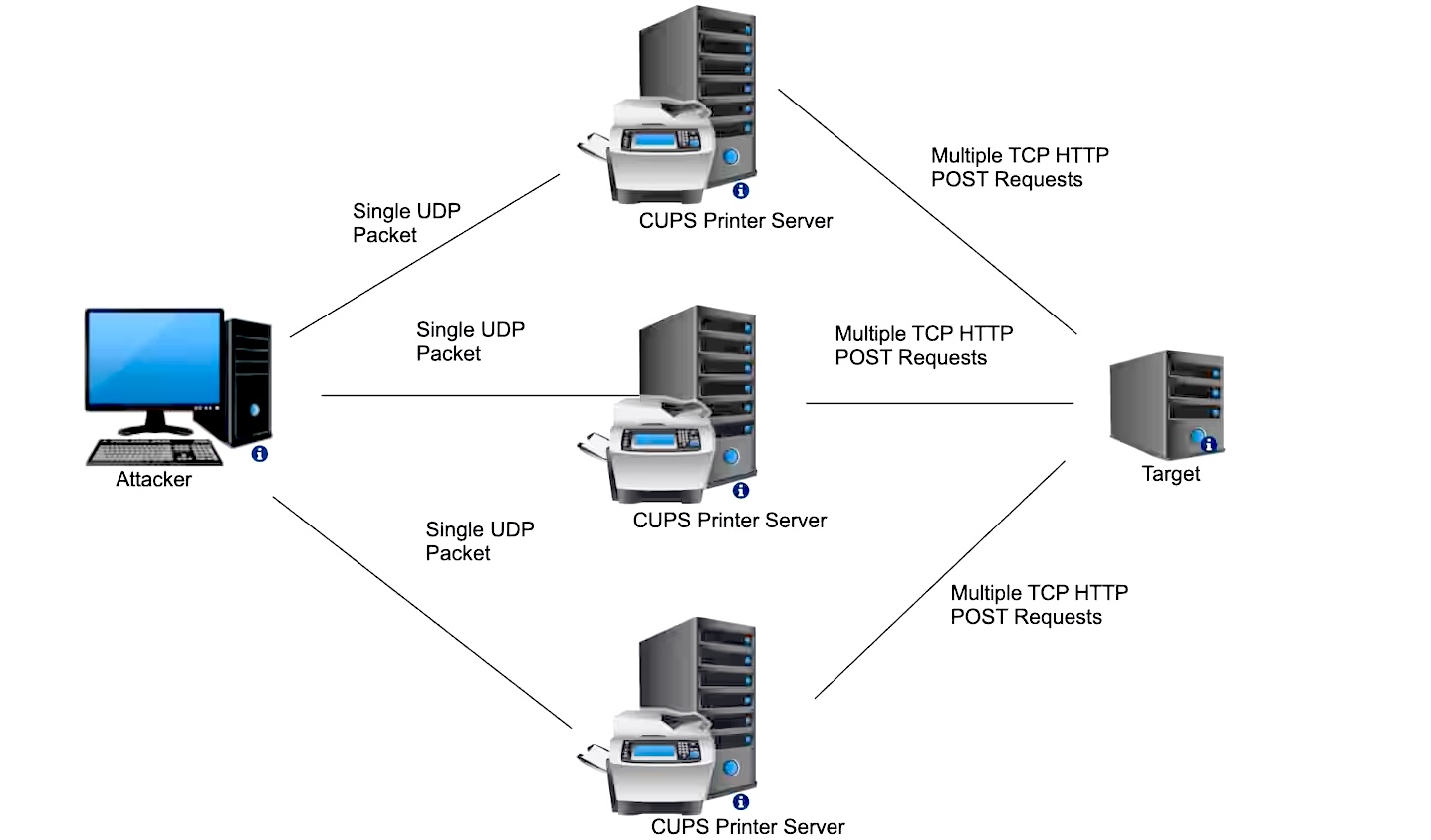
The vulnerability is triggered when an attacker sends a specifically crafted packet, tricking a CUPS server into treating a goal equivalent to a printer to be added.
Every packet despatched to weak CUPS servers prompts them to generate bigger IPP/HTTP requests directed to the goal gadget. This impacts each the vacation spot and the CUPS server, consuming their bandwidth and CPU assets.
Begins with a single malicious UDP packet
To provoke such an assault, a malicious actor solely must ship a single packet to an uncovered and weak CUPS service uncovered on-line. Akamai researchers estimate that round 58,000 servers, out of greater than 198,000 uncovered units, may very well be recruited for DDoS assaults.
Moreover, lots of of weak units demonstrated an “infinite loop” of requests, with some CUPS servers repeatedly sending requests after receiving an preliminary probe and a few servers getting into an countless loop in response to particular HTTP/404 errors.
Many of those weak machines had been working outdated variations of CUPS (relationship again to 2007), that are simple targets for cybercriminals who can exploit them to create botnets through the RCE chain or use them for DDoS amplification.
“Within the worst case situation, we noticed what gave the impression to be an countless stream of connection makes an attempt and requests on account of a single probe. These streams look like countless and can proceed till the daemon is killed or restarted.” Akamai researchers saying.
“Many of those techniques we noticed in testing established 1000’s of requests and despatched them to our testing infrastructure. In some circumstances, this conduct appeared to proceed indefinitely.”
Seconds wanted to carry out an assault
This DDoS amplification assault additionally requires minimal assets and little time to execute. Akamai warns {that a} risk actor might simply take management of all CUPS providers uncovered on the Web in a matter of seconds.
Directors are beneficial to deploy CVE-2024-47176 patches or disable the working of the cup searching service to dam potential assaults and mitigate the chance of their servers being added to a botnet or utilized in DDoS assaults.
“DDoS stays a viable assault vector used to harass and disrupt victims on the Web, from main industries and governments to small content material creators, on-line shops, and avid gamers,” Akamai researchers warned.
“Whereas the unique evaluation targeted on RCE, which might have a extra severe consequence, DDoS amplification can be simply abused on this case.”
Like Cloudflare revealed this weekits DDoS protection techniques needed to shield clients in opposition to a wave of L3/4 hypervolumetric DDoS assaults that reached 3.8 terabits per second (Tbps), the most important such assault ever recorded.

