Risk actors on
The assault, found by vx-undergroundIt’s a new variant of the “Click on repair“tactic that has turn out to be very fashionable amongst risk actors to distribute malware throughout the previous 12 months.
Nevertheless, quite than being fixes for widespread bugs, this variant is meant to be a captcha or verification system that customers should execute to hitch the channel.
Final month, Guardio Labs researchers and Infoblox researchers revealed a brand new marketing campaign which used CAPTCHA verification pages that requested customers to execute PowerShell instructions to confirm that they weren’t a bot.
Silk Street creator used as a decoy
Ross Ulbricht is the founder and foremost operator of the well-known darkish internet market Silk Street, which acted as a hub for the sale and buy of illicit items and companies.
The person was sentenced to life in jail in 2015, which some thought-about extreme provided that he facilitated the crimes and didn’t personally carry them out.
President Trump beforehand expressed the identical opinion, promising to pardon Ulbricht as soon as he turned president of the US, and yesterday stated fulfilled this promise.
Risk actors took benefit of this improvement, utilizing faux however verified Ross Ulbricht accounts on X to direct individuals to malicious Telegram channels introduced as official Ulbricht portals.
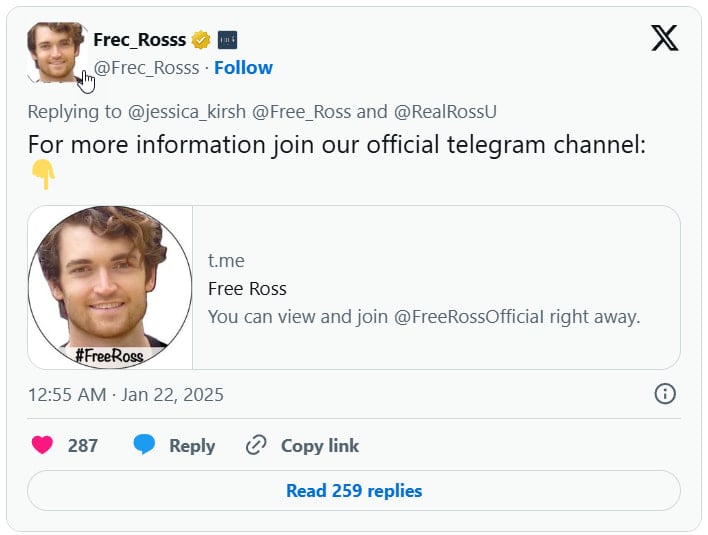
Supply: BleepingComputer
On Telegram, customers obtain a so-called id verification request known as ‘Safeguard’, which guides them via the faux verification course of.
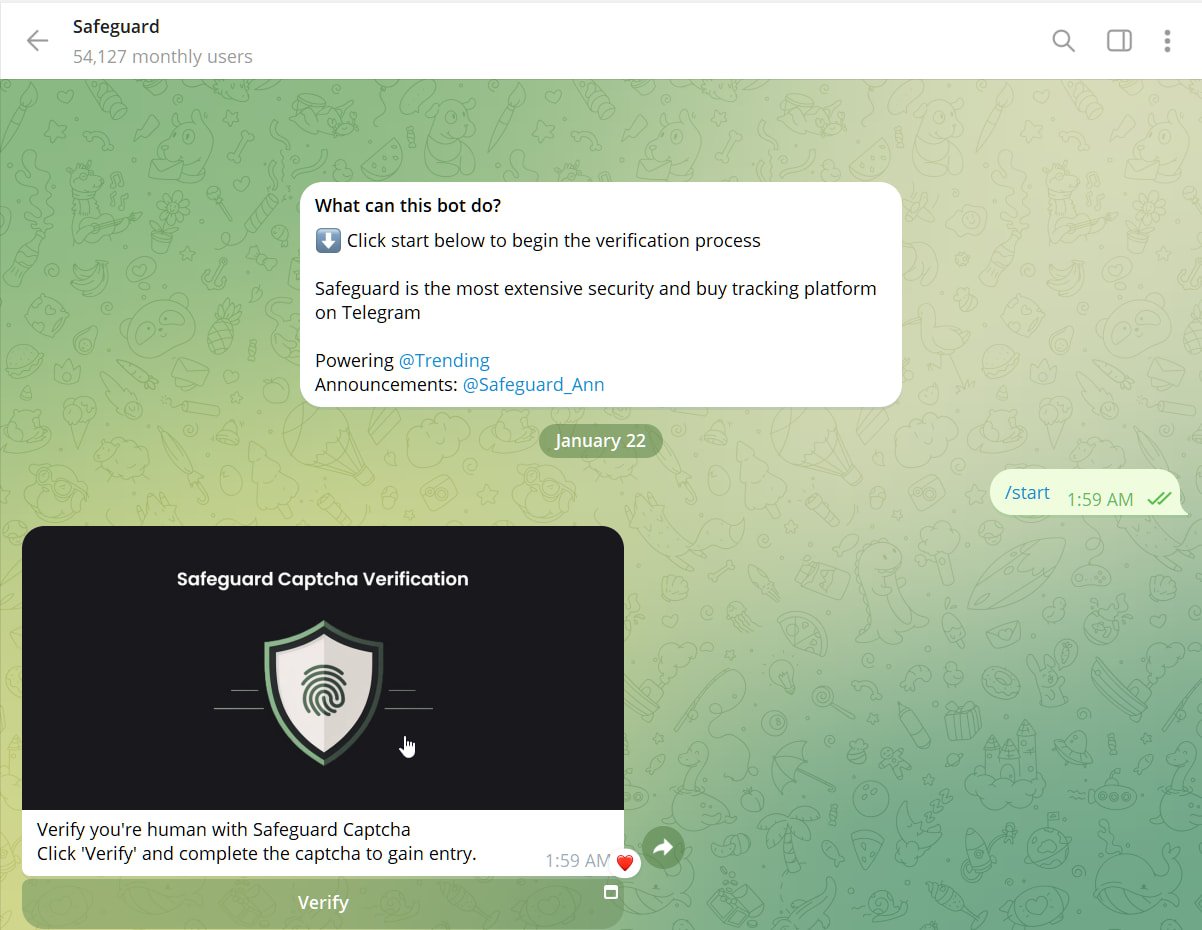
Supply: BleepingComputer
On the finish, customers are proven a Telegram Applet which reveals a faux verification dialog. This mini app routinely copies a PowerShell command to the machine’s clipboard after which prompts the consumer to open the Home windows Run dialog, paste it, and run it.
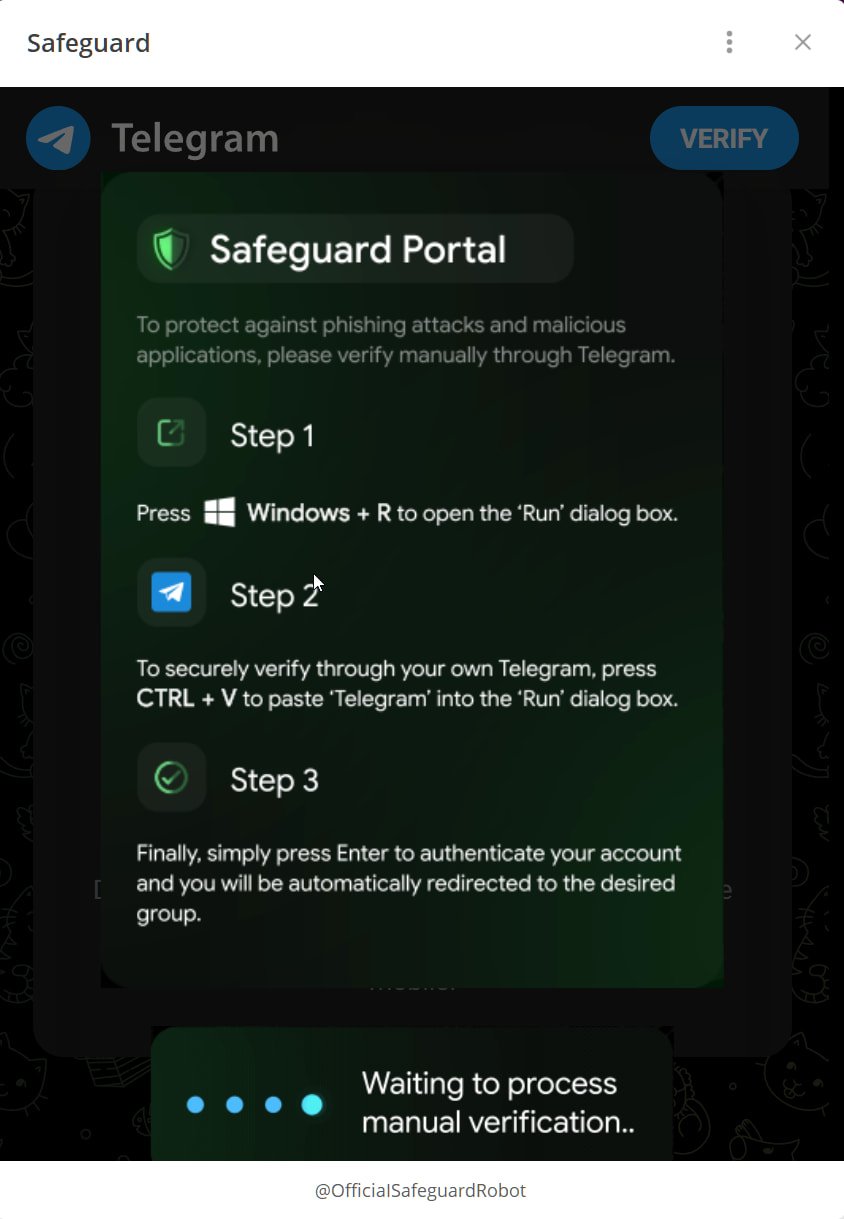
Supply: BleepingComputer
The code copied to the clipboard is downloaded and runs a PowerShell script, which finally downloads a ZIP file to http://openline(.)cyou.
This zip file accommodates quite a few recordsdata together with Id-helper.exe (VirusTotal), {that a} touch upon VirusTotal signifies it could be a Cobalt Strike charger.
Cobalt Strike is a penetration testing device generally utilized by risk actors to realize distant entry to the pc and networks they reside on. These kind of infections are sometimes precursors to ransomware assaults and knowledge theft.
The language used all through the verification course of is fastidiously chosen to keep away from elevating suspicion and sustaining the false verification premise.
Customers ought to by no means run something they copy on-line within the Home windows “Run” dialog field or PowerShell terminal until they know what they’re doing.
Should you’re unsure about one thing you copied to your clipboard, paste it right into a textual content reader and analyze its contents; any obfuscation will likely be thought-about a purple flag.

