The 2024 vacation season revealed a posh and evolving panorama for distributed service denial (DDOS). This 12 months’s tendencies included superior techniques, resembling a rise in DDOS-Alquiler operations, the Mass Botnets Meeting of DDOS by script youngsters, politically motivated assault campaigns and the derivation of CDN protections (Community content material supply) amongst different developed threats.
The 2024 vacation season revealed a posh and evolving panorama for distributed service denial (DDOS). This 12 months’s tendencies included superior techniques, resembling a rise in DDOS-Alquiler operations, the Mass Botnets Meeting of DDOS by script youngsters, politically motivated assault campaigns and the derivation of CDN protections (Community content material supply) amongst different developed threats.
The assault panorama of the 2024 vacation season in Azure
In the course of the vacation season, we discover a change in final 12 months’s assault patterns, highlighting how malicious actors regularly refine their techniques to keep away from ddos safety.
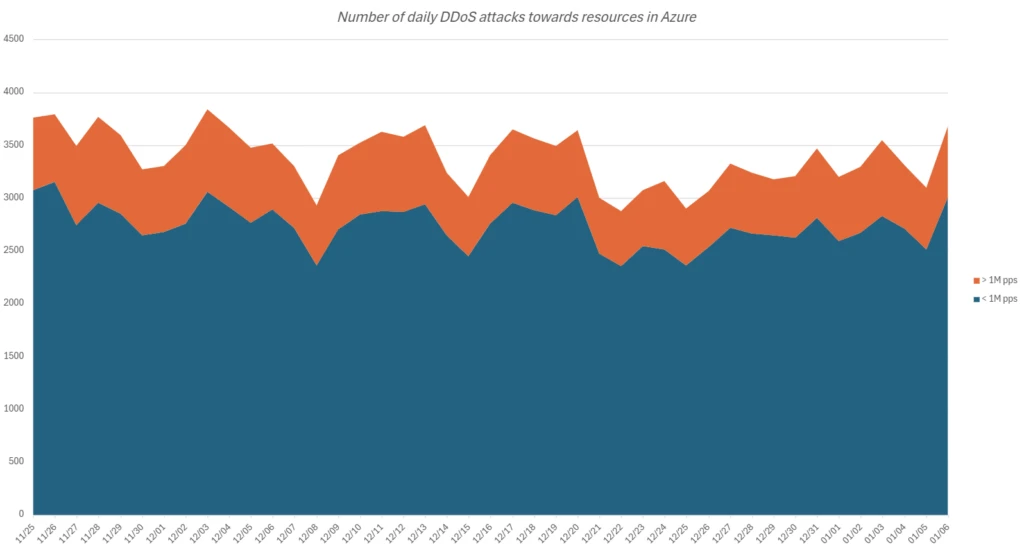
Every day assault quantity
Azure Mitiga Safety Infrastructure as much as 3,800 assaults each day. Giant -scale assaults of multiple million packages per second (PPS) characterize roughly 20% of those, just like Final 12 months evaluation. The extremely volumetric assaults that exceed 10 million PP are uncommon, solely 0.2% of all assaults, reflecting the target of the attackers to attenuate assets and keep away from detection.
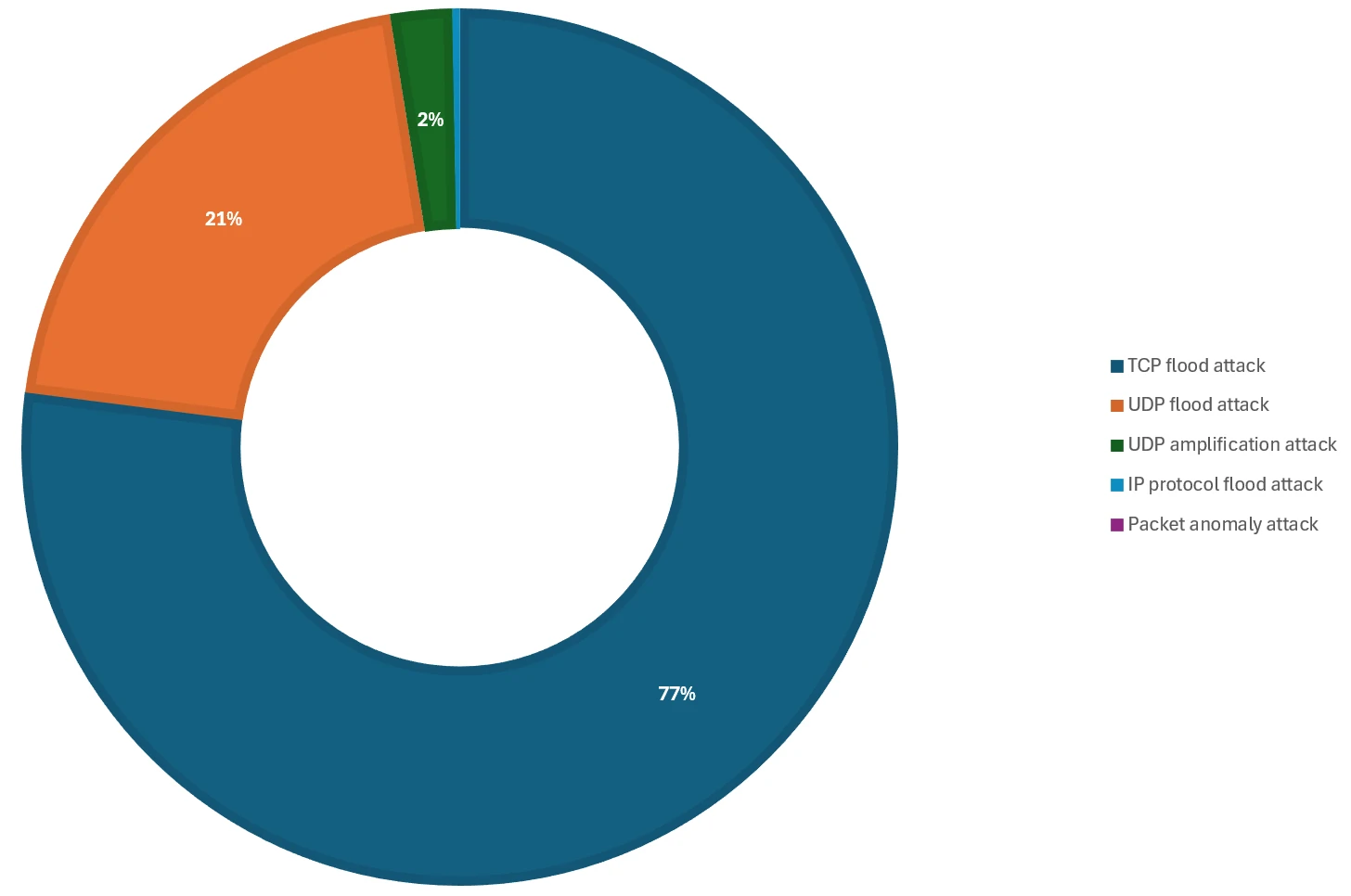
Assault protocols
The 2024 vacation season noticed a predominant use of TCP -based assaults (transport management protocol), aimed toward numerous functions and internet assets, representing 77% of the assaults. That is in distinction to final 12 months When UDP -based assaults (consumer information protocol) represented virtually 80% of assaults on video games and different assets. The primary TCP assault vectors this 12 months have been the floods TCP SYN (synchronized) and ACK (acknowledge).
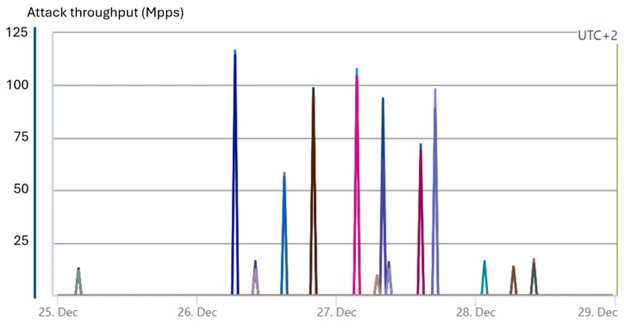
Azure blocks a large hurricane assault
A tremendous assault on sport assets reached 100-125 million PP in a number of waves. This assault, whose signatures are linked to Botnet HurricaneIt was utterly mitigated by Azure’s defenses.
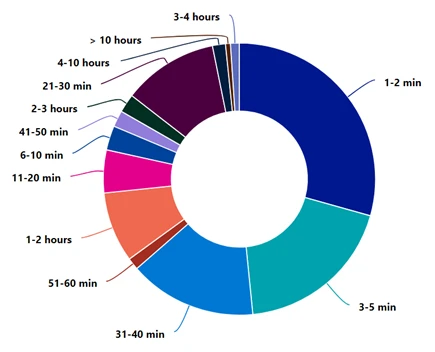
Period assaults
This vacation season once more witnessed the identical techniques of the adversaries to attempt to keep away from ddos mitigation methods by launching an explosion or brief -term assaults. 49% of all assaults lasted as much as 5 minutes, whereas 83% of the assaults lasted lower than 40 minutes. It’s insightful to know that any mitigation countermel to ddos that we implement to guard our utility ought to obtain efficient mitigation as quickly as attainable.
Political causes and over -the -ddos
This trip season, Azure’s assault tendencies replicate world patterns. Politically motivated assaultsPushed by geopolitical tensions, they persist. Ddos threats stay a major concern since new actors use instruments out there to trigger interruption.
The emergence of ddos-for rental providers, typically known as nerve-racking and beginning, has gained important recognition amongst attackers. These platforms, which could be simply accessed in cybercriminal boards, have democratized the flexibility to launch sturdy ddos assaults, which makes them attainable for much less refined criminals at minimal prices. Lately, there was a rise in each availability and using these providers. Throughout this vacation season, the appliance businesses of worldwide regulation carried out operations resembling Poweroff operation Final December, ensuing within the arrest of three people and the closure of 27 domains related to DDOS-to rent platforms. Regardless of these efforts, ddos nerve-racking proceed to thrive, providing quite a lot of strategies and assault energy, and it’s prone to persist of their prevalence.
Getting ready for 2025
The 2024 vacation season has emphasised the specter of the ddy assaults. Organizations should enhance their cybersecurity methods to counteract these evolving threats within the New 12 months. Strengthening defenses and staying attentive to new techniques is essential in 2025. Azure resistance in opposition to superior ddos threats highlights the significance of stable safety measures to guard digital belongings and assure the continuity of the enterprise.
Identification of publicity factors
Begin figuring out which of your functions is uncovered to public Web. Analysis of potential dangers And the vulnerabilities of those functions are essential to know the place you could be extra prone to assaults.
Recognizing regular operations
Familiarize your self with the conventional conduct of your functions. Azure offers monitoring providers and greatest practices that will help you acquire details about the well being of your functions and diagnose issues successfully.
Simulating assault situations
Usually Working Assault Simulation It’s an efficient solution to show the responses of their providers to attainable ddos assaults. In the course of the assessments, validates that their providers or functions proceed to perform as anticipated and that there aren’t any interruptions within the consumer expertise. Determine the gaps from the perspective of know-how and the method and incorpore them in your DDOS response technique.
Guarantee sturdy safety
With the excessive threat of ddos assaults, it’s important to have a safety service resembling DDOS safety. This service offers visitors monitoring all the time on, mitigation of automated assaults after detection, adaptive adjustment in actual time and the entire visibility of ddos assaults with telemetry, monitoring and alerts in actual time.
Layer Safety Implementation
For complete safety, set up a protection of a number of layers deploying ddos safety of Azure with Azure Internet Software Firewall (WAF). Azure DDOS safety ensures the community layer (layer 3 and 4), whereas Azure WAF save the appliance layer (layer 7). This mix ensures safety in opposition to numerous sorts of ddos assaults.
Alert settings
Azure ddos safety can determine and mitigate assaults with out consumer intervention. Alert settings For lively mitigations, you possibly can hold it knowledgeable in regards to the state of protected public IP assets.
Formulate a solution plan
Set a response workforce with clearly outlined roles and obligations. This workforce have to be an professional in figuring out, mitigating and monitoring an assault, in addition to coordinating with events and inside clients. Use simulation assessments to determine any hole in your response technique, guaranteeing that your workforce is ready for a number of assault situations.
Searching for professional help
Within the case of an assault, reaching technical professionals is important. Azure ddos safety shoppers have entry to Fast Ddos Reply (DRR) Assist gear throughout and after assaults. After an assault, proceed monitoring the assets and performs a retrospective evaluation. Apply studying to enhance your DDOS response technique, guaranteeing higher preparation for future incidents.
Name to motion
The 2024 vacation season highlighted the state of affairs of threats in evolving ddos assaults, with a major enhance in DDOS-Alquiler, mass botnets operations and political motivation campaigns. These threats emphasize the necessity for sturdy ddos safety and a DDOS response plan. Azure helps organizations to remain forward of those threats. Clients should allow the safety of a number of layers deploying DDOS safety with Azure Internet Software Firewall (WAF). As well as, clients ought to Allow telemetry and Alert capabilities to watch and reply to lively mitigations successfully.

