A generalized Phishing marketing campaign has been aimed toward nearly 12,000 github repositories with false “safety alert” issues, dishonest builders to authorize a malicious Oauth utility that provides the attackers complete management over their accounts and code.
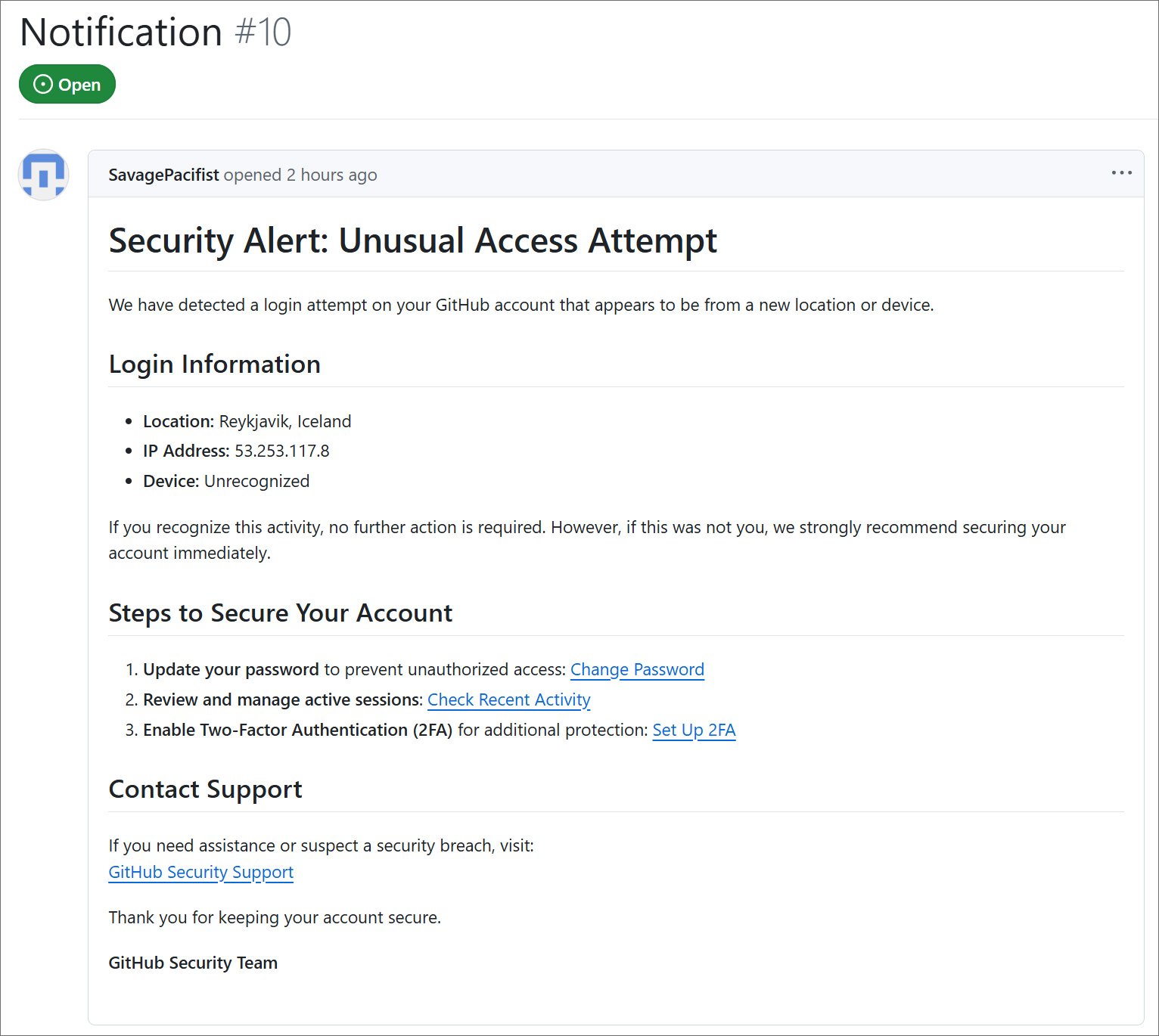
“Security alert: uncommon entry try we’ve detected an login try at your Github account that appears to be a brand new location or machine,” says the pHishing downside of Github.
All Github Phishing issues include the identical textual content, warning customers that it was an uncommon exercise of their Reykjavik account, Iceland and IP 53,253,117.8 deal with.
Supply: Bleepingcomter
The cybersecurity researcher Luc4M noticed for the primary time the false safety alert, which warned GitHub customers that their account was raped and that they need to replace their password, overview and handle lively periods, and allow two components authentication to make sure their accounts.
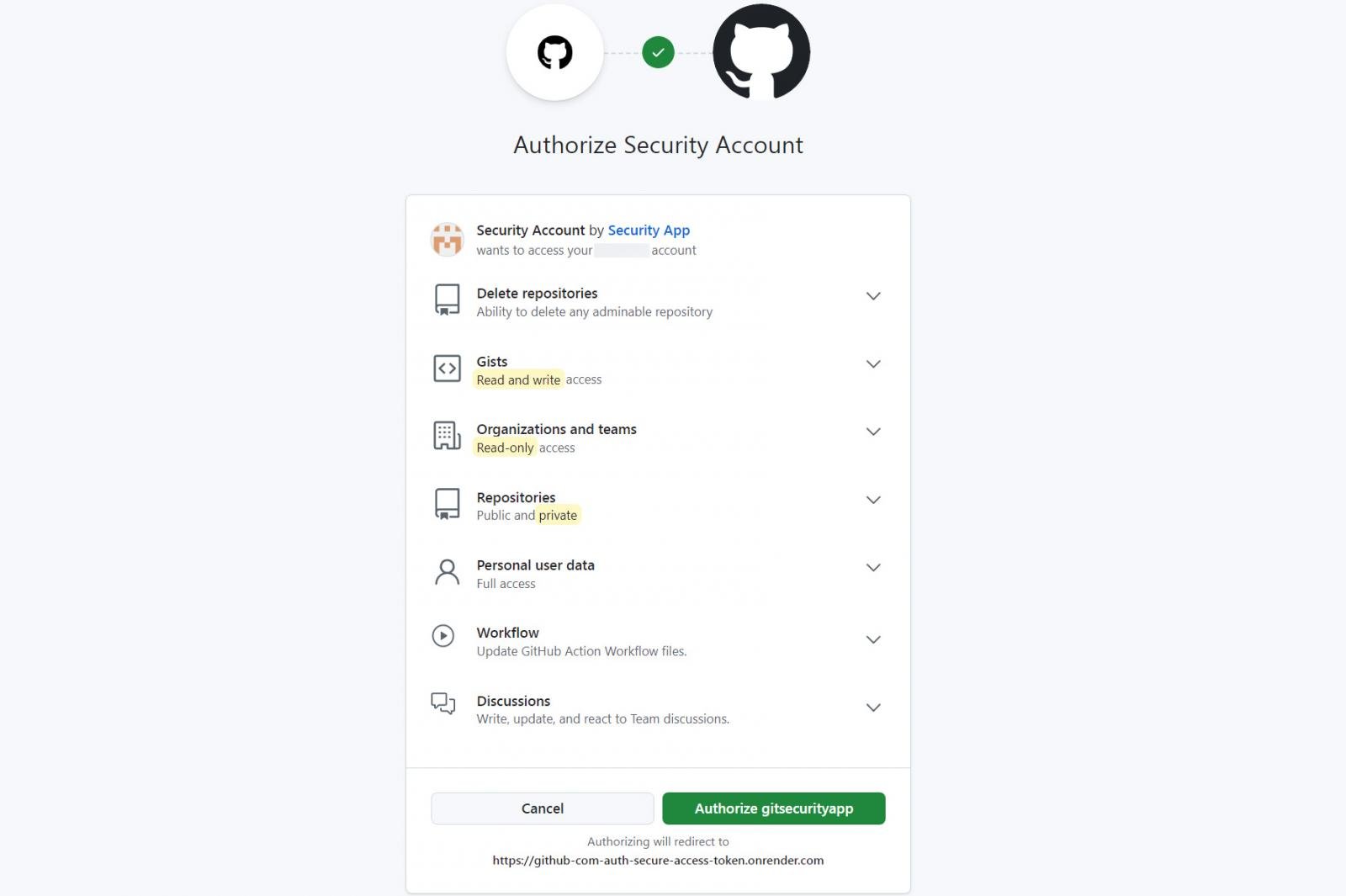
Nonetheless, all hyperlinks for these advisable actions result in a GitHub authorization web page for an OAUTH “gitsecuritypp” utility that requests many very dangerous permits (ESCPA) and would enable an attacker full entry to the account and repositories of a person.
Supply: Bleepingcomter
The requested permits and the entry they supply are listed under:
- Repo: Grants full entry to private and non-private repositories
- person: Capacity to learn and write on the person profile
- Learn: Org: Learn the membership of the group, the organizational tasks and membership tasks
- Learn: dialogue, Write: dialogue: Learn and write entry to discussions
- essence: Entry to Github Gists
- Delete_repo: Permission to get rid of repositories
- Workflows, workflow, writing: workflow, learn: workflow, replace: work stream: Management on the workflows of Github’s actions
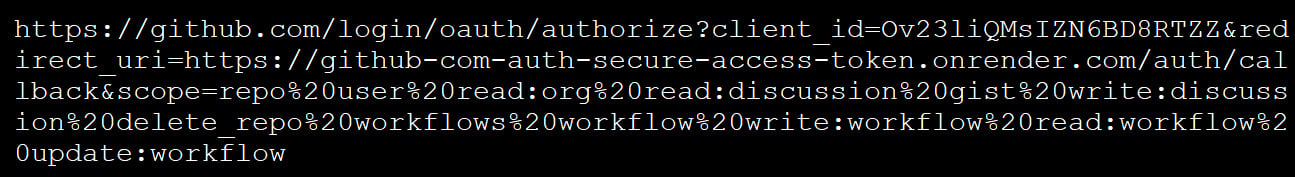
If a github person logs and authorizes the Malicious Software Oauth, an entry token will generate and be despatched to the appliance refund deal with of the appliance, which on this marketing campaign has been a number of web sites hosted on Onrender.com (Render).
Supply: Bleepingcomter
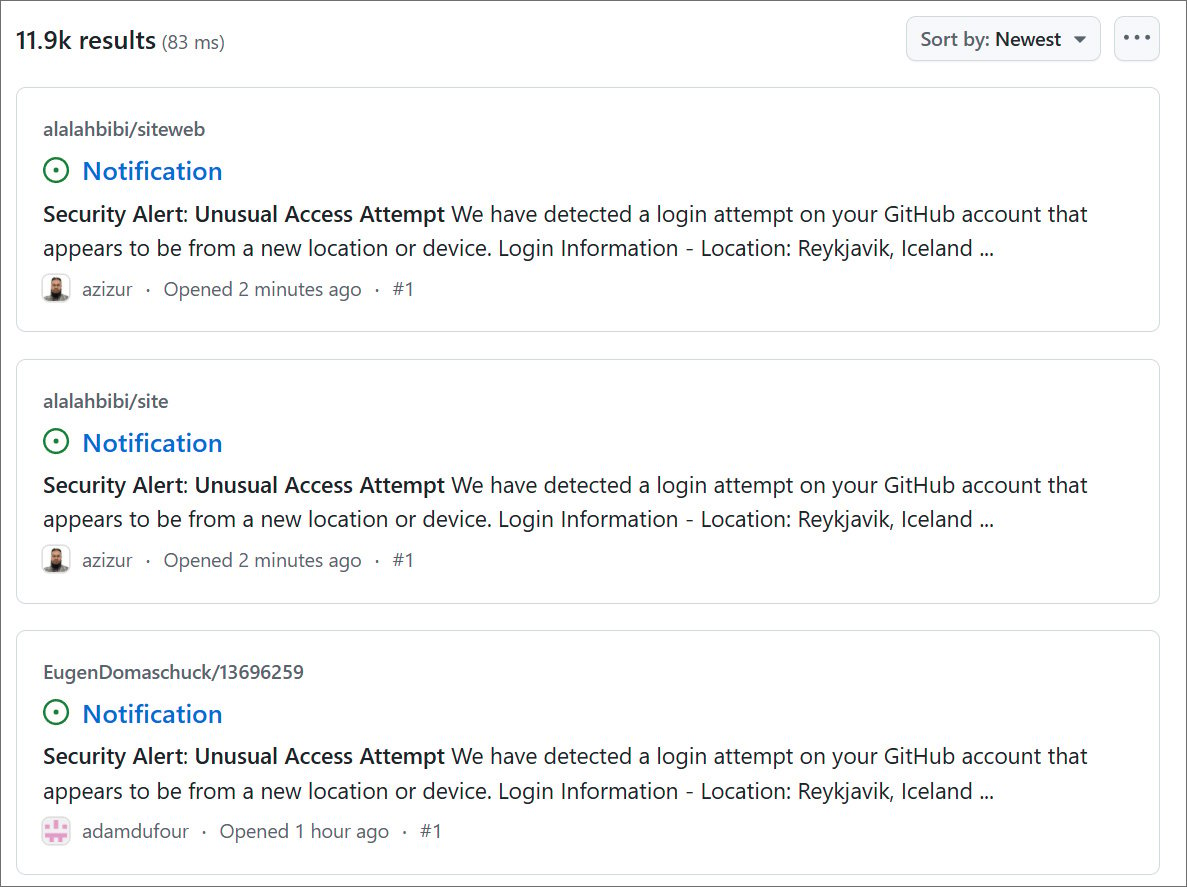
The Phishing marketing campaign started this morning at 6:52 am et and is ongoing, with nearly 12,000 repositories led within the assault. Nonetheless, the quantity fluctuates, indicating that Github most likely responds to the assault.
Supply: Bleepingcomter
If this Phishing assault impacted it and by mistake gave authorization to the Malicious Oauth utility, you could instantly revoke your entry whenever you enter the GitHub configuration after which functions.
From the appliance display, revoke entry to any github utility or OAUTH functions that aren’t acquainted or suspected. On this marketing campaign, you could search for functions named just like ‘gitsecuritypp’.
Then you could search for new or sudden Github actions (workflows) and if personal GISTS have been created.
Lastly, flip your credentials and authorization tokens.
Bleepingcomuter contacted Github in regards to the Phishing and Udpacha marketing campaign this story once we obtain a solution.


