The infamous APT hacking group generally known as FIN7 has launched a community of pretend deep nude producing websites powered by synthetic intelligence to contaminate guests with information-stealing malware.
FIN7 is believed to be a Russian hacking group that has been finishing up monetary fraud and cybercrime since 2013, with hyperlinks to ransomware gangs corresponding to darkish facet, Black Matterand BlackCat, who lately carried out an exit rip-off after stealing 20 million {dollars} UnitedHealth Ransom Cost.
FIN7 is understood for its subtle phishing and social engineering assaults, corresponding to impersonating BestBuy to ship malicious USB keys or making a faux safety firm rent pentesters and builders for ransomware assaults with out them understanding.
Subsequently, it’s not shocking to find that they’ve now been linked to an intricate community of internet sites selling AI-powered deep nude mills that declare to create faux nude variations of images of clothed folks.
The expertise has been controversial for the hurt it will possibly trigger to topics by creating express non-consensual pictures, and has even been banned in lots of locations all over the world. Nonetheless, curiosity on this expertise stays robust.
A community of deepnude mills
FIN7 faux deep nude websites function traps for folks curious about producing faux deep nudes of celebrities or different folks. In 2019, risk actors I used the same lure to unfold information-stealing malware even earlier than the explosion of AI.
The deepnude generator community operates underneath the identical model title “AI Nude” and promotes itself by black hat search engine optimization ways to rank websites excessive in search outcomes.
In accordance Silent pushFIN7 immediately operated websites corresponding to “aiNude(.)ai”, “easynude(.)web site” and nude-ai(.)professional”, which provided “free trials” or “free downloads”, however in actuality solely unfold malware. .
All websites use the same design that guarantees the flexibility to generate free AI deep nude pictures from any uploaded picture.
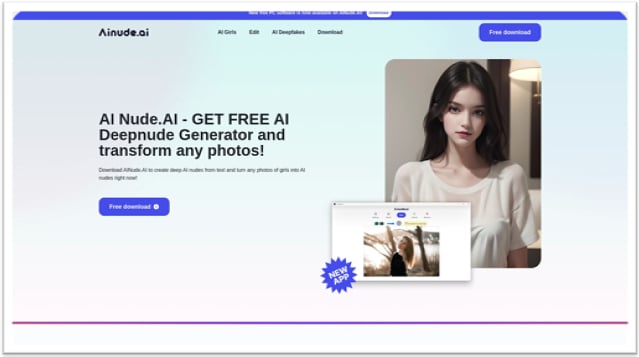
Supply: Silent Push
Faux web sites permit customers to add pictures they wish to create deepfake nudes. Nonetheless, after performing the supposed “deepnude”, it’s not displayed on the display screen. As a substitute, the consumer is prompted to click on a hyperlink to obtain the generated picture.
Doing so will take the consumer to a different website that shows a password and a hyperlink to a password-protected file hosted on Dropbox. Whereas this website continues to be energetic, the Dropbox hyperlink now not works.
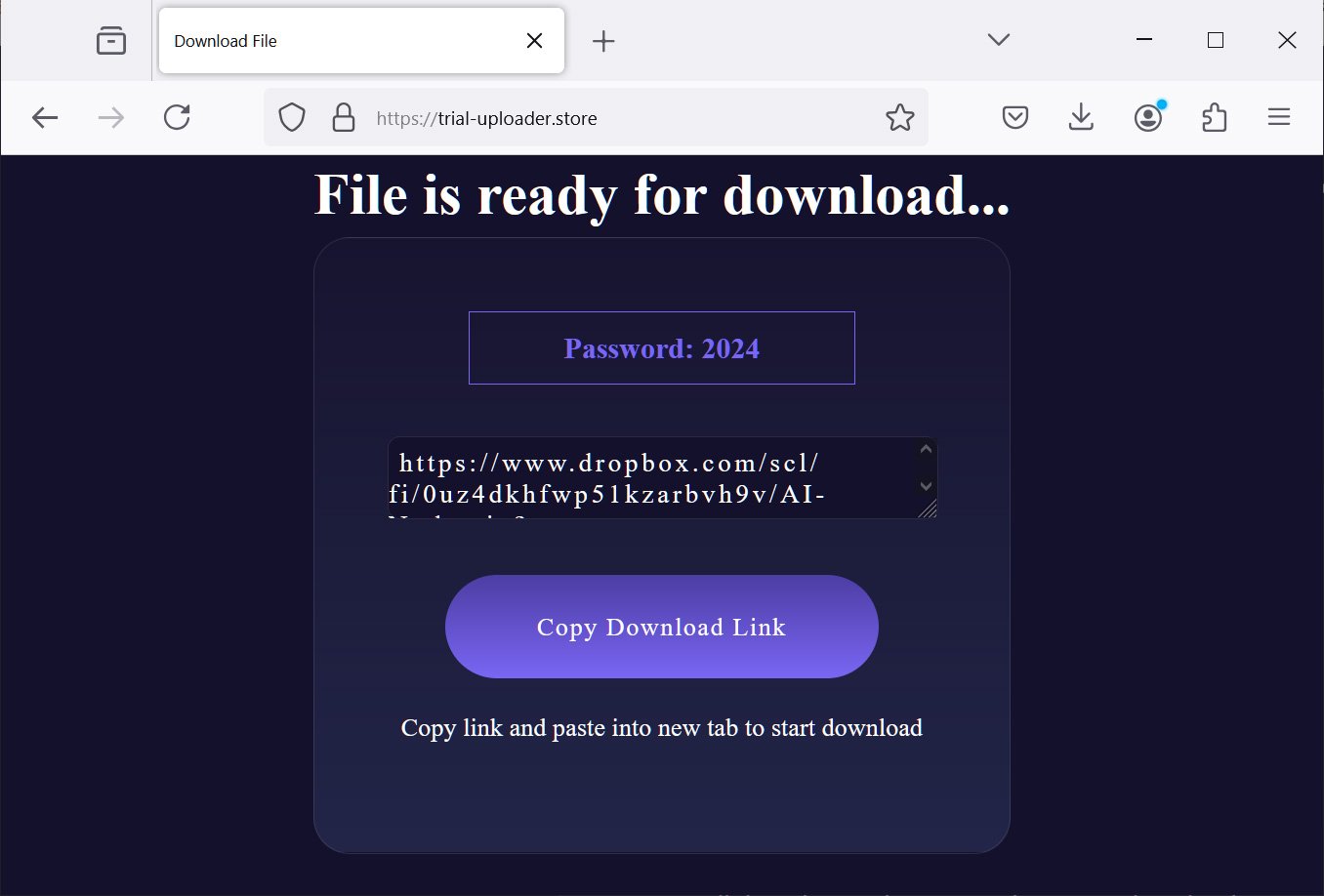
Supply: BleepingComputer
Nonetheless, as an alternative of a deep nude picture, the file comprises the information-stealing malware Lumma Stealer. When executed, the malware will steal credentials and cookies saved in internet browsers, cryptocurrency wallets, and different information from the pc.
Silent Push additionally noticed some websites selling a deepnude era program for Home windows that might as an alternative implement Redline Stealer and D3F@ck Loader, that are additionally used to steal data from compromised gadgets.
All seven websites detected by Silent Push have since been eliminated, however customers who could have downloaded recordsdata from them ought to contemplate themselves contaminated.
Different FIN7 campaigns
Silent Push additionally recognized parallel FIN7 campaigns launching NetSupport RAT by web sites that ask guests to put in a browser extension.
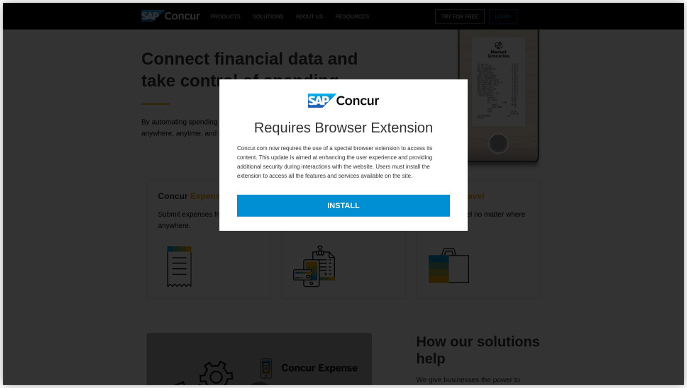
Supply: Silent Push
In different circumstances, FIN7 makes use of payloads that seem to spoof well-known manufacturers and functions corresponding to Cannon, Zoom, Fortnite, Fortinet VPN, Razer Gaming, and PuTTY.
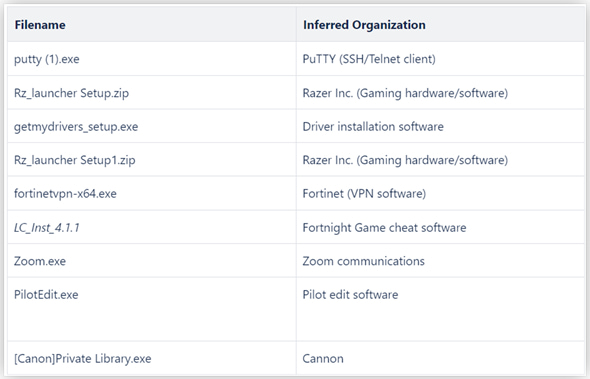
Supply: Silent Push
These payloads will be distributed to victims utilizing search engine optimization ways and malvertising, tricking them into downloading Trojanized installers.
FIN7 was lately uncovered for promoting his customized EDR Elimination Device “AvNeutralizer” to different cybercriminals, Aimed toward IT workers at automakers. in phishing assaults, and Deploying Cl0p ransomware in assaults in opposition to organizations.

