An lively marketing campaign of a risk actor probably linked to Russia is aimed toward Microsoft 365 accounts of people in organizations of curiosity utilizing the phishing of the gadget code.
The goals are within the authorities, NGOs, IT companies and know-how, protection, telecommunications, well being and vitality/oil and fuel sectors in Europe, North America, Africa and the Center East.
Microsoft’s Intelligence Heart of Microsoft tracks the risk actors behind the pHishing marketing campaign of the gadget code comparable to ‘Storm-237’, primarily based on curiosity, victimology and tradecraft, researchers have a mean confidence that the exercise is related to a state-state operation that aligns with Russia pursuits.
System code phishing assaults
Restricted enter gadgets: Those that lack keyboard or browser assist, comparable to sensible televisions and a few IoT, belief a code authentication circulate to permit customers to log in to an software by writing an authorization code on a separate gadget as A smartphone or a pc.
Microsoft researchers found that since final August, Storm-2372 abuses this authentication circulate by deceiving customers to enter codes of gadgets generated by attackers in authentic login pages.
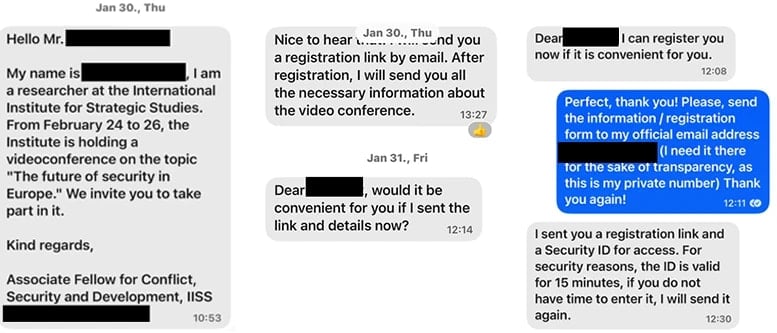
The operations provoke the assault after first establishing a reference to the target “making a distinguished particular person related to the target” on messaging platforms comparable to WhatsApp, Sign and Microsoft Groups.
Supply: Microsoft
The risk actor step by step establishes a relationship earlier than sending a false invitation within the on-line assembly by electronic mail or message.
In accordance with the researchers, the sufferer receives a staff assembly invitation that features a gadget code generated by the attacker.
“Invites entice the consumer to finish an software code authentication software that emulates the messaging service expertise, which supplies preliminary entry Storm-2372 to victims accounts and permits graphic API knowledge assortment actions, comparable to the e-mail assortment “, Microsoft says.
This offers the pc pirates entry to the sufferer’s Microsoft companies (electronic mail, cloud storage) with out the necessity for a password whereas stolen tokens stay legitimate.
Supply: Microsoft
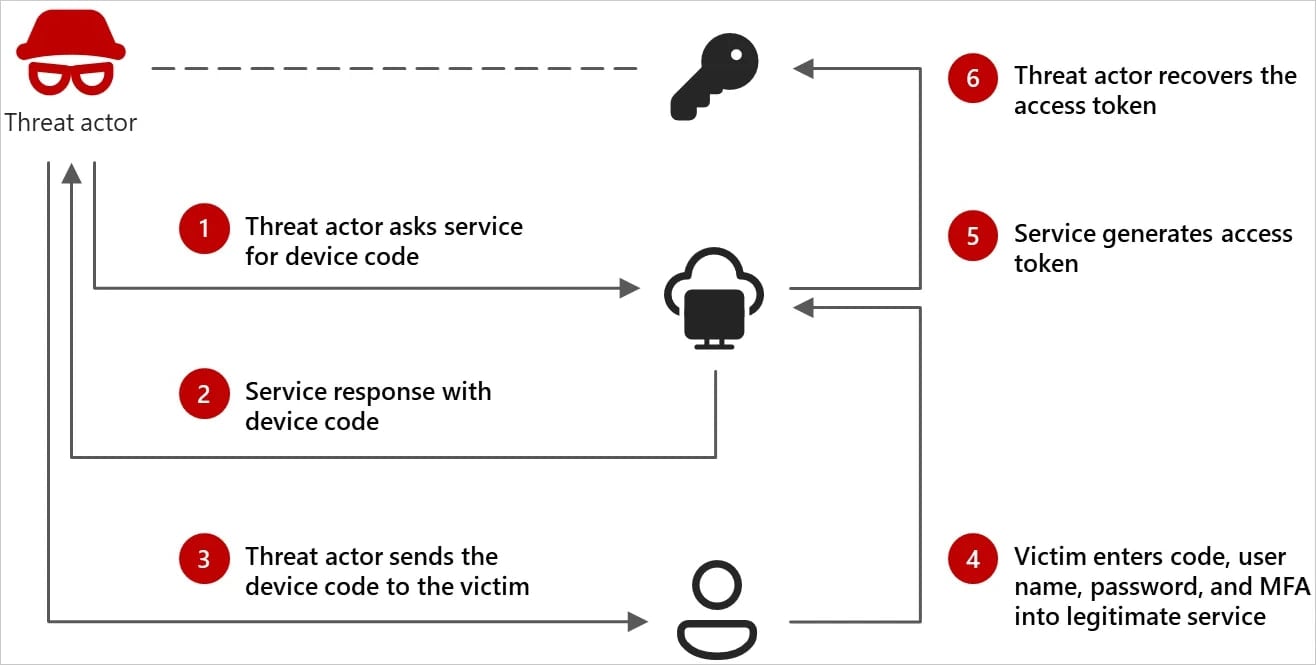
Nevertheless, Microsoft says that the attacker is now utilizing the precise buyer ID for Microsoft’s authentication hall within the gadget code login circulate, which permits them to generate new tokens.
This opens new probabilities of assault and persistence, for the reason that risk actor can use buyer identification to register Entrra ID gadgets, the Microsoft cloud -based entry administration resolution.
“With the identical replace token and the brand new id of the gadget, Storm-2372 can get hold of a principal replace token (PRT) and entry the sources of a corporation. We’ve noticed storm-2372 utilizing the linked gadget to gather digital emails,” —- Microsoft
Defend towards Storm-2372
To counteract the phishing assaults of the gadget code utilized by Storm-2372, Microsoft proposes System gadget code lock when potential and making use of conditional entry insurance policies in Microsoft enters ID to restrict its use to gadgets or belief networks.
If the phishing of the gadget code is suspected, instantly revokes the consumer replace tokens utilizing ‘Revokesigninsionesions’ and set up a conditional entry coverage to pressure re-authorization for affected customers.
Lastly, use Microsoft’s login information in Entrra ID to watch and shortly establish excessive volumes of authentication makes an attempt in a brief interval, gadget code session late gadget despatched to a number of customers.

