Two botnets tracked as ‘Ficora’ and ‘Capsaicin’ have recorded elevated exercise focusing on D-Hyperlink routers which have reached the tip of their helpful life or are operating outdated firmware variations.
The goal record consists of widespread D-Hyperlink units utilized by people and organizations reminiscent of DIR-645, DIR-806, GO-RT-AC750, and DIR-845L.
For preliminary entry, the 2 items of malware use identified exploits for CVE-2015-2051, CVE-2019-10891, CVE-2022-37056, and CVE-2024-33112.
As soon as a tool is compromised, attackers exploit weaknesses within the D-Hyperlink administration interface (HNAP) and execute malicious instructions by way of a GetDeviceSettings motion.
Botnets can steal information and execute shell scripts. Attackers seem to compromise units for distributed denial of service (DDoS) functions.
Ficora has a large geographic distribution with some deal with Japan and america. Capsaicin seems to be primarily focusing on units in East Asian international locations and elevated its exercise for simply two days, beginning on October 21.
Fícora botnet
Ficora is a more moderen variant of the Mirai botnet, particularly tailor-made to use flaws in D-Hyperlink units.
In accordance Fortinet telemetry informationThe botnet shows random targets, with two notable spikes in exercise throughout October and November.
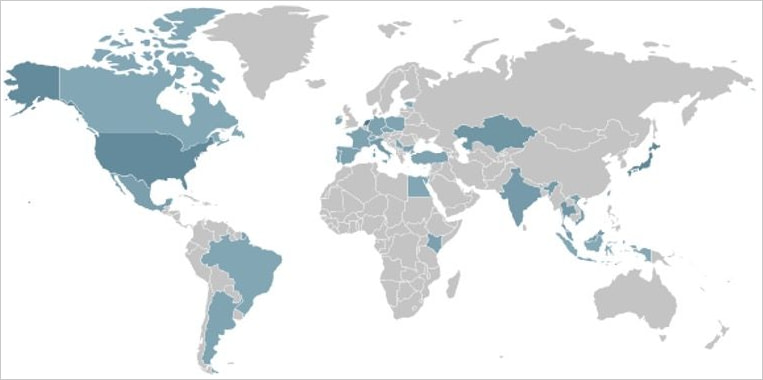
Supply: Fortinet
After gaining preliminary entry on D-Hyperlink units, Ficora makes use of a shell script known as ‘multi’ to obtain and execute its payload by way of a number of strategies reminiscent of acquire, curl, ftpgetand ftp.
The malware features a built-in brute pressure element with encrypted credentials to contaminate further Linux-based units, whereas supporting a number of {hardware} architectures.
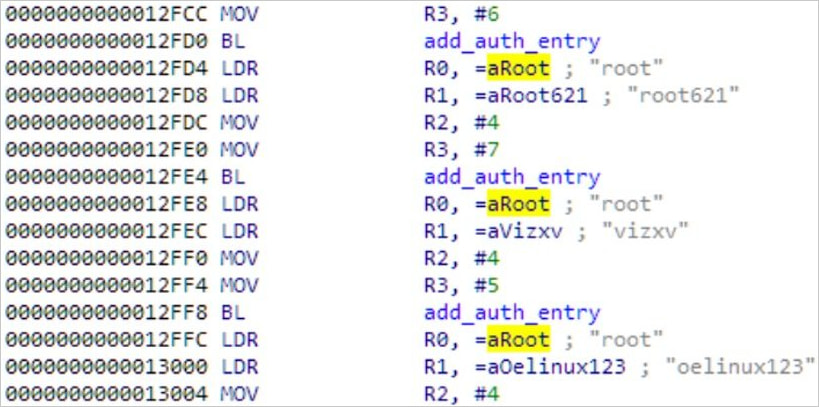
Supply: Fortinet
As for its DDoS capabilities, it helps UDP flooding, TCP flooding, and DNS amplification to maximise the ability of its assaults.
Capsaicin zombie community
Capsaicin is a variant of the Kaiten botnet and is believed to be malware developed by the Keksec group, identified for ‘enemy robotic‘ and different malware households focusing on Linux units.
Fortinet solely noticed it in a collection of assaults between October 21 and 22, primarily focusing on international locations in East Asia.
The an infection happens by way of a obtain script (“bins.sh”), which retrieves binaries prefixed with ‘yakuza’ for various architectures, together with arm, mips, sparc, and x86.
The malware actively appears to be like for different botnet payloads which might be lively on the identical host and disables them.
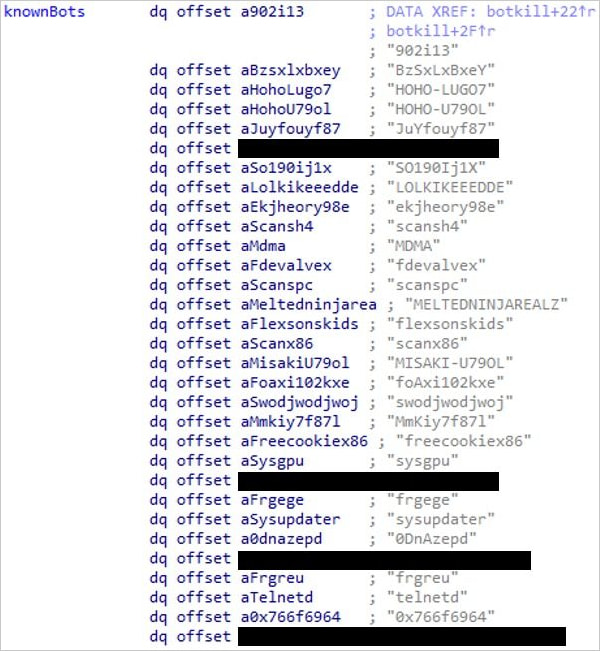
Supply: Fortinet
Along with its DDoS capabilities, which mirror these of Ficora, Capsaicin may acquire info from the host and leak it to the command and management (C2) server for monitoring.
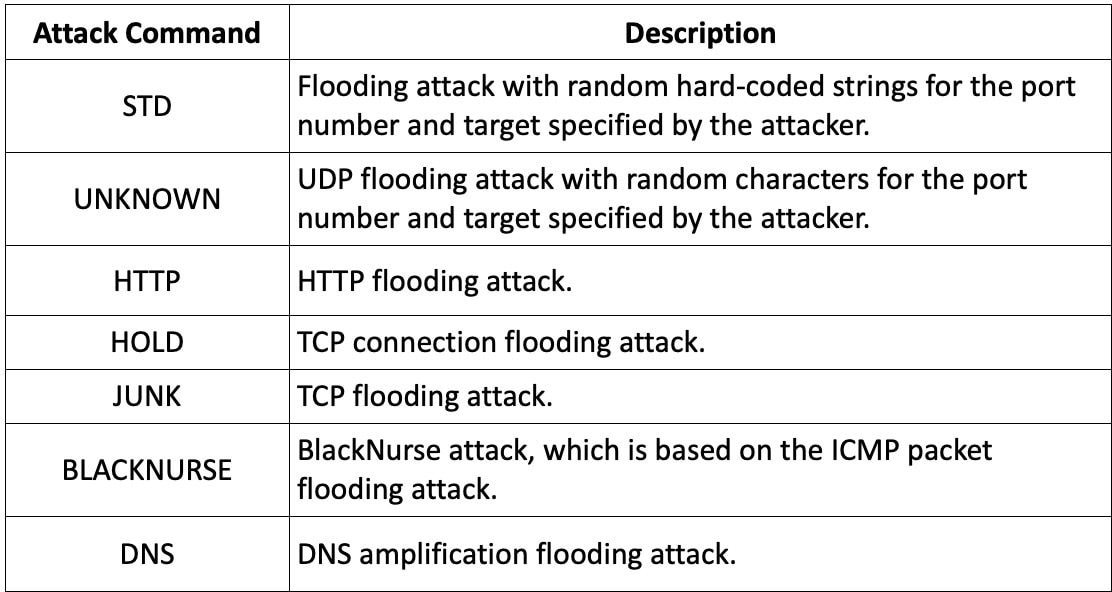
Supply: Fortinet
Protection towards botnets
One technique to stop botnet malware infections on routers and IoT units is to make sure they’re operating the most recent model of firmware, which ought to deal with identified vulnerabilities.
If the machine has reached the tip of its helpful life and is now not receiving safety updates, it needs to be changed with a brand new mannequin.
As a basic tip, you need to change default administrator credentials with sturdy, distinctive passwords and disable distant entry interfaces if they aren’t wanted.

