New investigation has found extra hyperlinks between Black Sufficient and Cactus Ransomware, with members of each teams that use the identical social engineering assaults and Proxy BackConction malware for entry to exploitation to company networks.
In January, Zscaler found A Zloader malware pattern containing what gave the impression to be a brand new DNS tunnel perform. Additional Walmart analysis He indicated that Zloader was dropping a brand new proxy malware referred to as BackConnect that contained code references to the QBOT malware (qakbot).
Backconnect is malware that acts as a proxy device for distant entry to compromised servers. Backconnect permits cybercriminals in tunnel site visitors to obfusce their actions and intensify assaults inside the environment of a sufferer with out being detected.
It’s believed that each Zloader, QBOT and Backconnect are linked to the operation of black ransomware sufficient, members who use malware to violate and unfold via company networks.
These ties are additional strengthened by a current BlackBasta information leaks That introduced the interior conversations of the operation, together with these between the Ransomware gang supervisor and somebody who’s believed to be the QBOT developer.
The hyperlinks
Black is sufficient is a ransomware gang that Launched in April 2022. It’s believed that it consists of members of the Ransomware Conti gang, which off in Could 2022 After struggling Huge information leakage of the supply code and inside conversations.
The ransomware gang has traditionally been Qakbot used for preliminary entry to company networks. Nonetheless, after a 2023 Legislation utility operation When interrupted QBOt’s operations, Operation Black has sufficient has sought various malware to violate the networks.
The group pivot for BackConnect means that they’re nonetheless working with builders linked to the QBOt operation.
In New Pattern Micr reportOr, researchers have discovered that the cactus ransomware group can also be utilizing the assault connection in assaults, indicating a potential overlap within the members between each teams.
Within the black assaults of Sufficient and Cactus seen by Pattern Micro, the risk actors used the identical social engineering assault to bombard an goal with an amazing variety of emails, a Techniques typically related to Black Sufficient.
The risk actors would talk with the goal via Microsoft tools, passing an worker of the assistance desk, finally, deceiving the sufferer to supply distant entry via Home windows Fast Help.
Whereas the circulate of assaults for the black assaults of Sufficient and Cactus shouldn’t be an identical, they have been very related, and the pattern meets the cactus risk actor who makes use of command and management servers typically related to Black Sufficient.
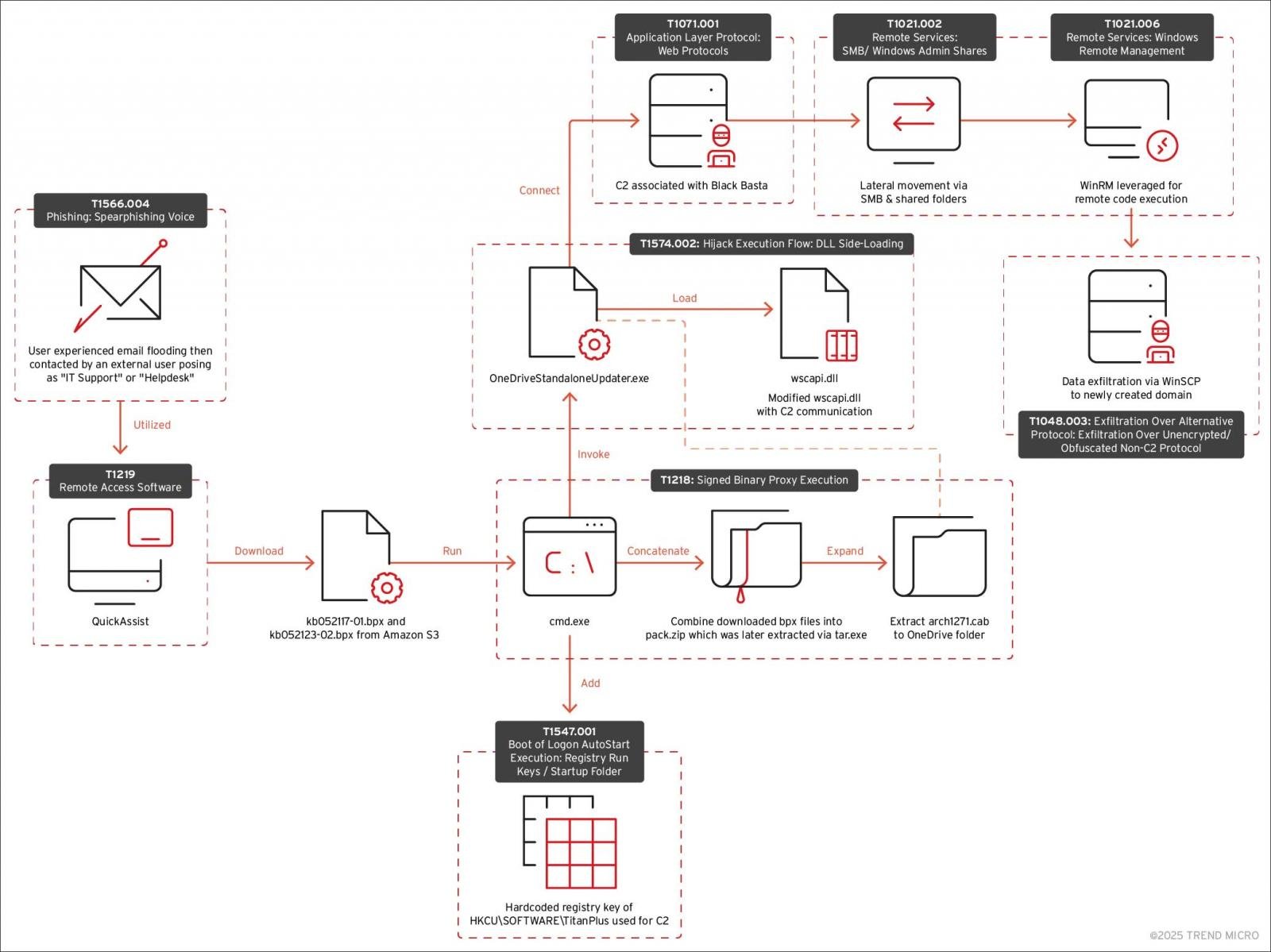
Supply: Pattern Micro
The cactus ransomware emerged in early 2023 and since then has directed quite a lot of organizations that use techniques much like Black Sufficient’s.
Bleepingcomuter’s earlier stories In Cactus, he additionally confirmed hyperlinks between the 2 ransomware gangs, with cactus utilizing a Powershell script referred to as Totorexec that was typically seen in black ransomware assaults sufficient.
As well as, the Black Pandilla Sufficient Ransomware adopted an encryption routine that was initially unique to cactus ransomware assaults, much more strengthening ties between each teams.
The shared use of techniques, the border and different operational similarities ask questions on whether or not cactus ransomware is a black model change sufficient or just an overlap between members.
Nonetheless, Bleepingcomuter has discovered that Black has been slowly fading since December 2024, with its off -line escape website for many of 2025.
It’s believed that a lot of Black’s members had sufficient to maneuver to different ransomware gangs, akin to cactus, with the current information filtration the final nail within the coffin.

