New particulars have emerged a couple of phishing marketing campaign concentrating on Chrome browser extension builders that led to the compromise of no less than thirty-five extensions to inject data-stealing code, together with these from cybersecurity firm Cyberhaven.
Though preliminary experiences Specializing in the Cyberhaven security-focused extension, subsequent investigations revealed that the identical code had been injected into no less than 35 extensions used collectively by roughly 2,600,000 individuals.
From experiences on LinkedIn and Google Teams From particular builders, the most recent marketing campaign began round December 5, 2024. Nevertheless, the earlier command and management subdomains discovered by BleepingComputer existed as early as March 2024.
“I simply needed to alert individuals a couple of extra refined than common phishing electronic mail we obtained indicating a violation of the shape Chrome extension coverage: ‘Pointless particulars in description,'” the focused put up reads to the Chromium Extension group of the Google group.
“The hyperlink on this electronic mail seems to be like the net retailer, however directs to a phishing web site that may attempt to take management of your Chrome extension and doubtless replace it with malware.”
A misleading OAuth assault chain
The assault begins with a phishing electronic mail despatched to Chrome extension builders immediately or through a help electronic mail related to their area identify.
Of the emails considered by BleepingComputer, the next domains had been used on this marketing campaign to ship phishing emails:
supportchromestore.com
forextensions.com
chromeforextension.com
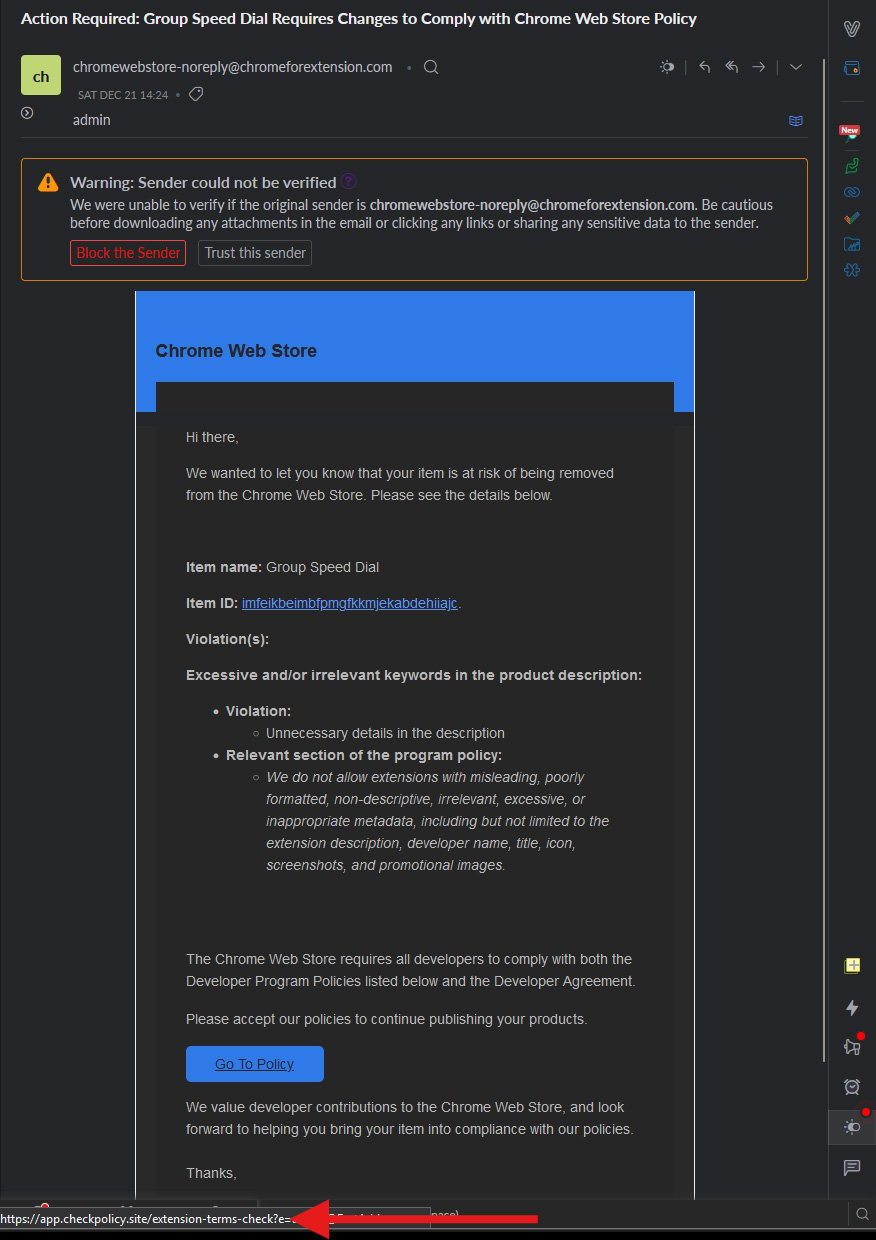
The phishing electronic mail, which seems to return from Google, claims that the extension violates Chrome Internet Retailer insurance policies and is liable to being eliminated.
“We don’t enable extensions with deceptive, poorly formatted, non-descriptive, irrelevant, extreme or inappropriate metadata, together with however not restricted to the extension description, developer identify, title, icon, screenshots and promotional photos “, reads the phishing. electronic mail.
Particularly, the extension developer is led to consider that the outline of their software program comprises deceptive info and should conform to the Chrome Internet Retailer insurance policies.
Supply: Google Teams
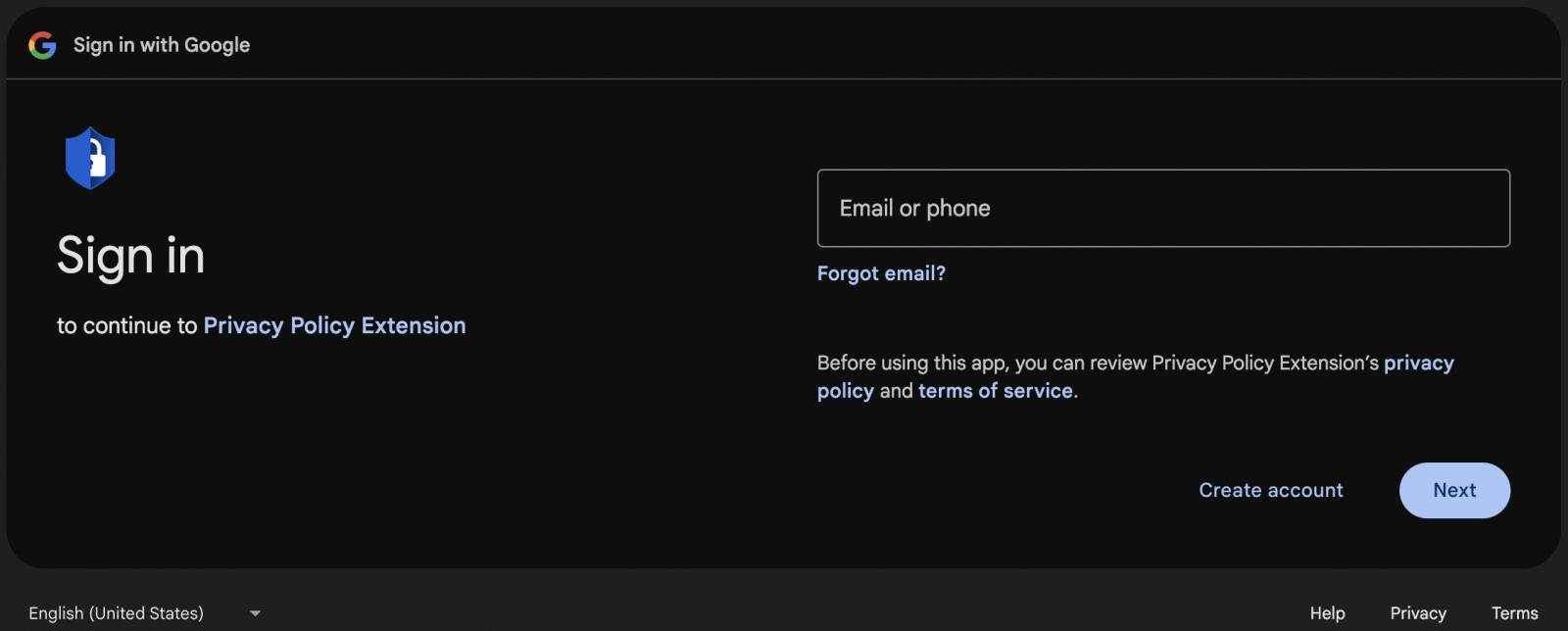
If the developer clicks the built-in ‘Go to Coverage’ button in an effort to know what guidelines they’ve violated, they’re directed to a official login web page on Google’s area for a malicious OAuth software.
The web page is a part of Google’s commonplace authorization stream, designed to securely grant permissions to third-party functions to entry particular Google account sources.
Supply: Cyberhaven
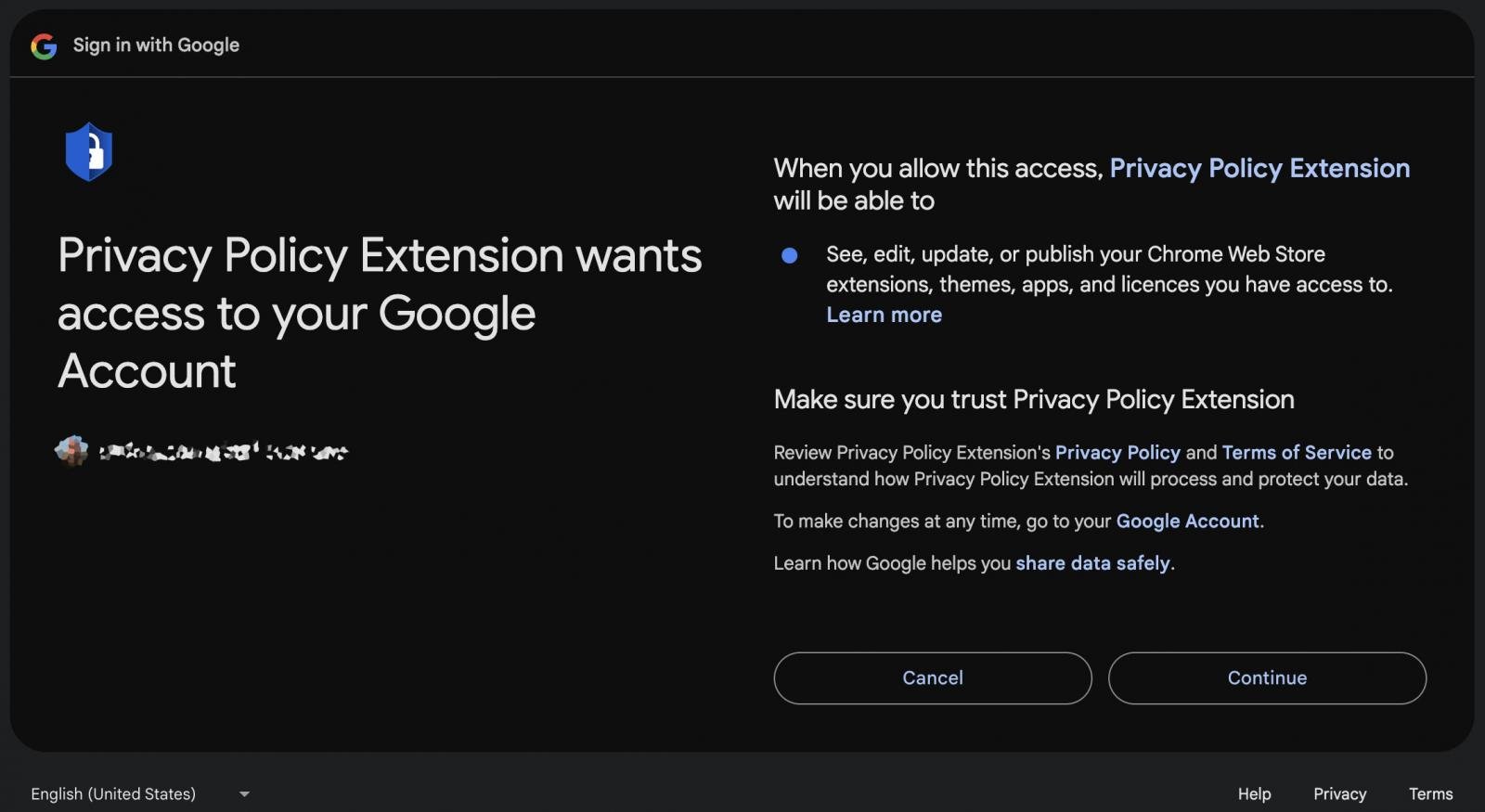
On that platform, the attacker hosted a malicious OAuth software referred to as “Privateness Coverage Extension” that requested the sufferer to grant permission to handle Chrome Internet Retailer extensions via their account.
“Whenever you enable this entry, the Privateness Coverage Extension will be capable to: View, edit, replace, or publish the Chrome Internet Retailer extensions, themes, apps, and licenses to which it has entry,” the OAuth authorization web page reads .
Supply: Cyberhaven
Multi-factor authentication didn’t assist safe the account, as direct approvals will not be required in OAuth authorization flows and the method assumes the consumer absolutely understands the scope of the permissions it’s granting.
“The worker adopted the usual stream and inadvertently licensed this malicious third-party software.” Cyberhaven explains in a autopsy report.
“The worker had Google Superior Safety enabled and had MFA overlaying their account. The worker didn’t obtain an MFA discover. The worker’s Google credentials weren’t compromised.”
As soon as the risk actors gained entry to the extension’s developer account, they modified the extension to incorporate two malicious recordsdata, specifically ’employee.js’ and ‘content material.js’, which contained code to steal information from Fb accounts.
The hijacked extension was then printed as a “new” model on the Chrome Internet Retailer.
Whereas Extension Whole tracks thirty-five extensions affected by this phishing marketing campaign, the assault COIs point out {that a} a lot bigger quantity had been focused.
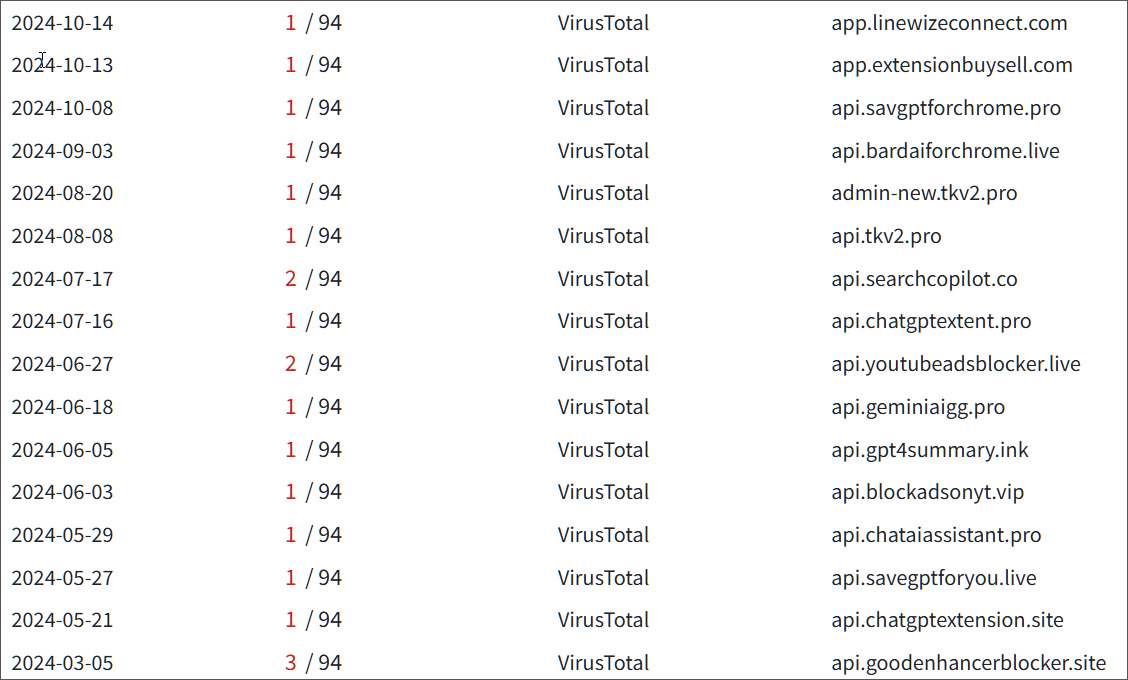
In accordance VirusTotalRisk actors beforehand registered domains for particular extensions, even when they didn’t fall for the assault.
Whereas a lot of the domains had been created in November and December, BleepingComputer found that risk actors had been testing this assault in March 2024.
Supply: BleepingComputer
Goal Fb Enterprise Accounts
Evaluation of the compromised machines confirmed that the attackers had been looking for the Fb accounts of customers of the poisoned extensions.
Particularly, the information theft code tried to acquire the consumer’s Fb ID, entry token, account info, advert account info, and enterprise accounts.
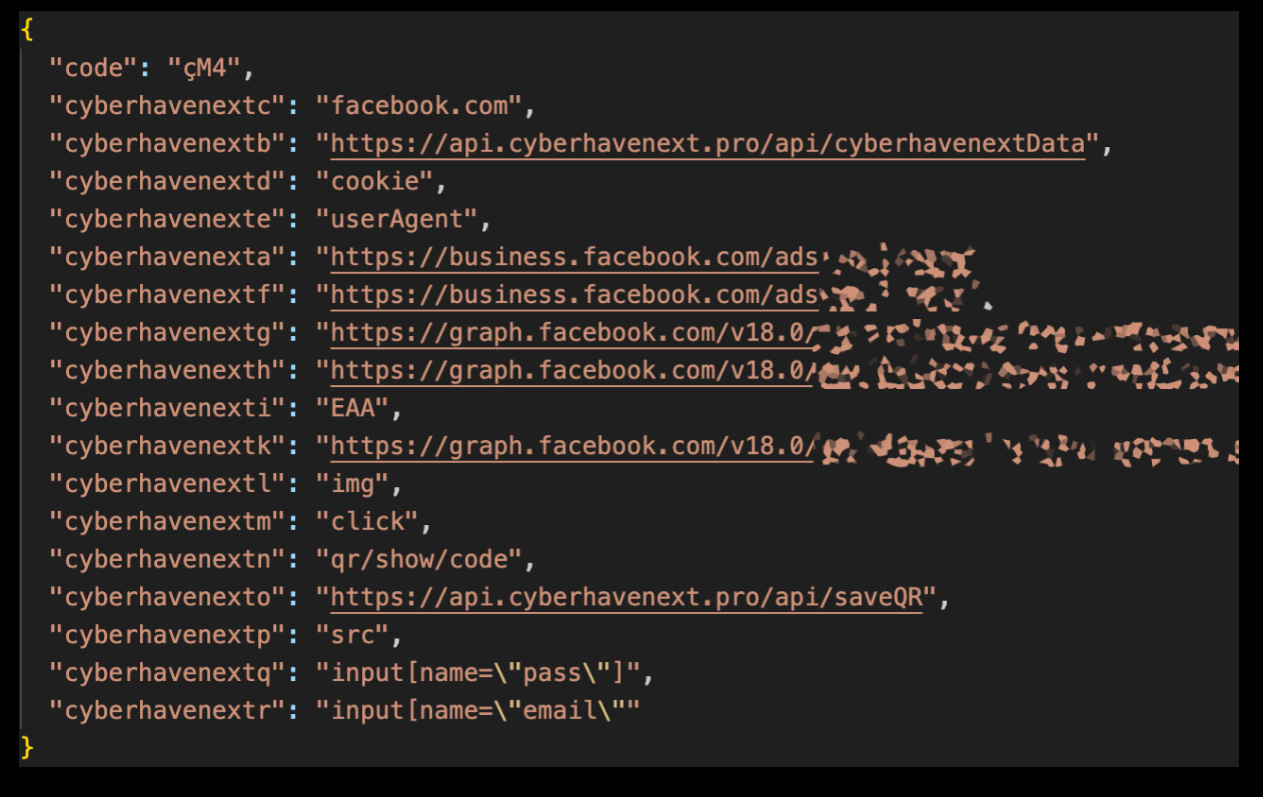
Supply: Cyberhaven
Moreover, the malicious code added a mouse click on occasion listener particularly for the sufferer’s interactions on Fb.com, searching for QR code photos associated to the platform’s two-factor authentication or CAPTCHA mechanisms.
This was supposed to bypass 2FA protections on the Fb account and permit risk actors to hijack it.
The stolen info can be packaged along with Fb cookies, consumer agent string, Fb ID, and mouse click on occasions and leaked to the attacker’s command and management (C2) server.
Risk actors have been goal Fb enterprise accounts via a number of avenues of assault to make direct funds from the sufferer’s credit score to their account, run disinformation or phishing campaigns on the social media platform, or monetize their entry by promoting it to others.

