A brand new ransomware operator known as ‘Mora_001’ is exploiting two Fortinet vulnerabilities to acquire unauthorized entry to Firewall home equipment and implement a customized ransomware pressure known as Superblack.
The 2 vulnerabilities, each derivations of authentication, are CVE-2024-55591 and CVE-2025-24472, which Fortinet revealed in January and February, respectively.
When Fortinet first revealed CVE-2024-55591 on January 14, they confirmed that it had been exploited as a zero dayWith the Arctic Wolf affirming that it had been Utilized in assaults since November 2024 To violate the Foregate Firewalls.
Confusedly, on February 11, Fortinet added CVE-2025-2447 to its January discoverwhich led many to consider that it was a freshly exploited defect. Nonetheless, Fortinet advised Bleepingcomter that this error was additionally solved in January 2024 and was not exploited.
“We have no idea that CVE-2025-24472 has been exploited,” Fortinet advised Bleepingcomter at the moment.
Nonetheless, a brand new report of Froscout researchersHe says they found the SuperBlack assaults on the finish of January 2025, with the menace actor utilizing CVE-2025-24472 as quickly as February 2, 2025.
“Whereas Foresout itself didn’t immediately report the exploitation of 24472 to Fortinet, since one of many affected organizations we work with was to share the outcomes of our analysis with the PSirt de Fortinet staff,” Froscout advised Bleepingcomuter.
“Shortly after, Fortinet up to date his discover on February 11 to acknowledge CVE-2025-24472 as actively exploited.”
Bleepingcomuter contacted Fortinet to make clear this level, however we’re nonetheless ready for a solution.
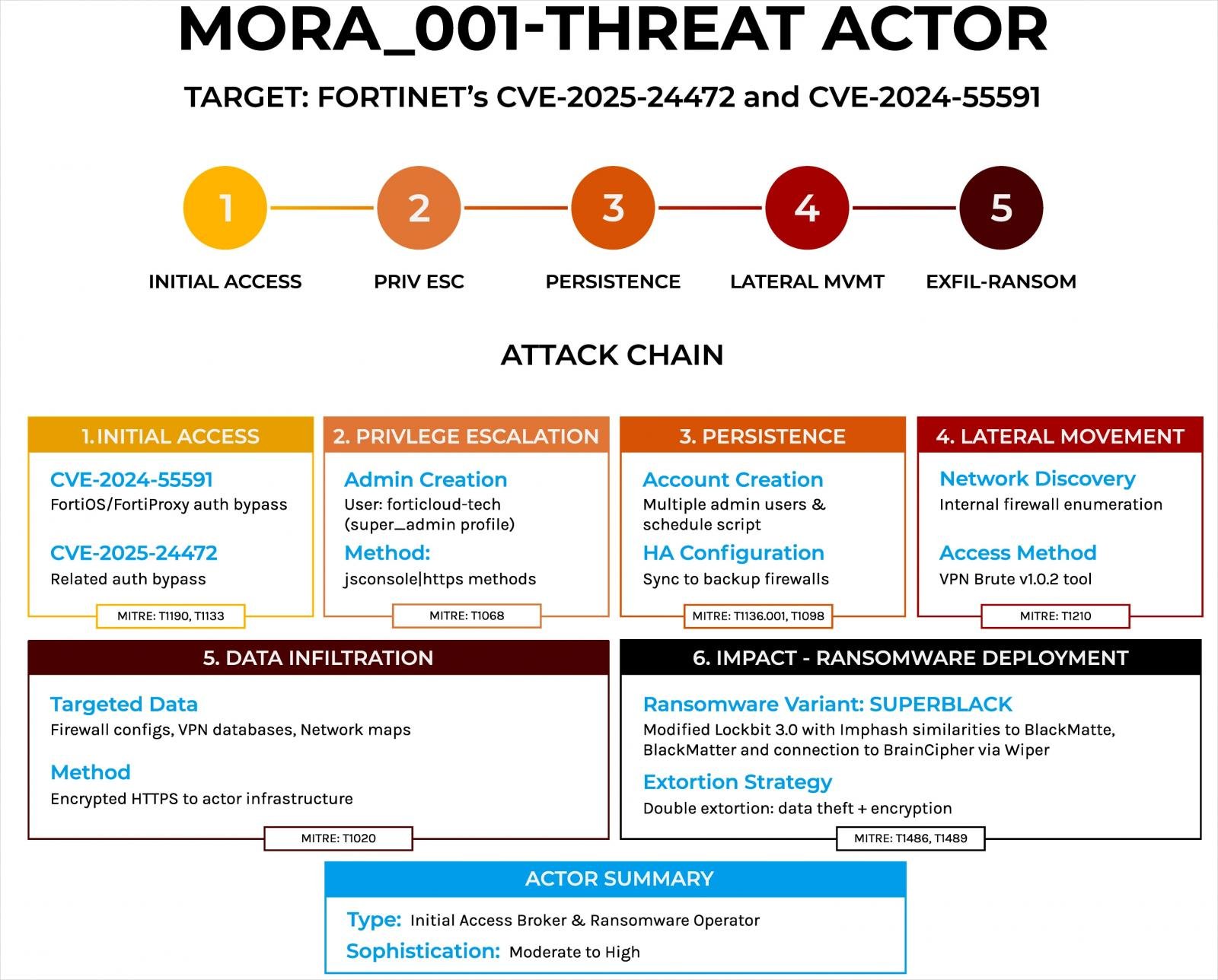
Superblack Ransomware Assaults
Foresout says that Ransomware Mora_001 operator follows a extremely structured assault chain that doesn’t range a lot among the many victims.
First, the attacker wins the super_admin privileges by exploiting the 2 Fortinet failures utilizing websockt -based assaults via the JSCONSole interface or sending direct requests from HTTPS to uncovered Firewall interfaces.
Subsequent, they create new administrator accounts (Forticloud-Tech, Forigigate-Firewall, Adnimistrator) and modify automation duties to recreate them if they’re eradicated.
Supply: Forecout
After this, the attacker maps the community and tries a lateral motion utilizing stolen VPN credentials and just lately mixture VPN accounts, Home windows Administration Instrumentation (WMIC) and SSH, and Tacacs+/Radius authentication.
Mora_001 steals knowledge utilizing a customized device earlier than encrypting information for double extortion, prioritizing knowledge base information and servers and area controllers.
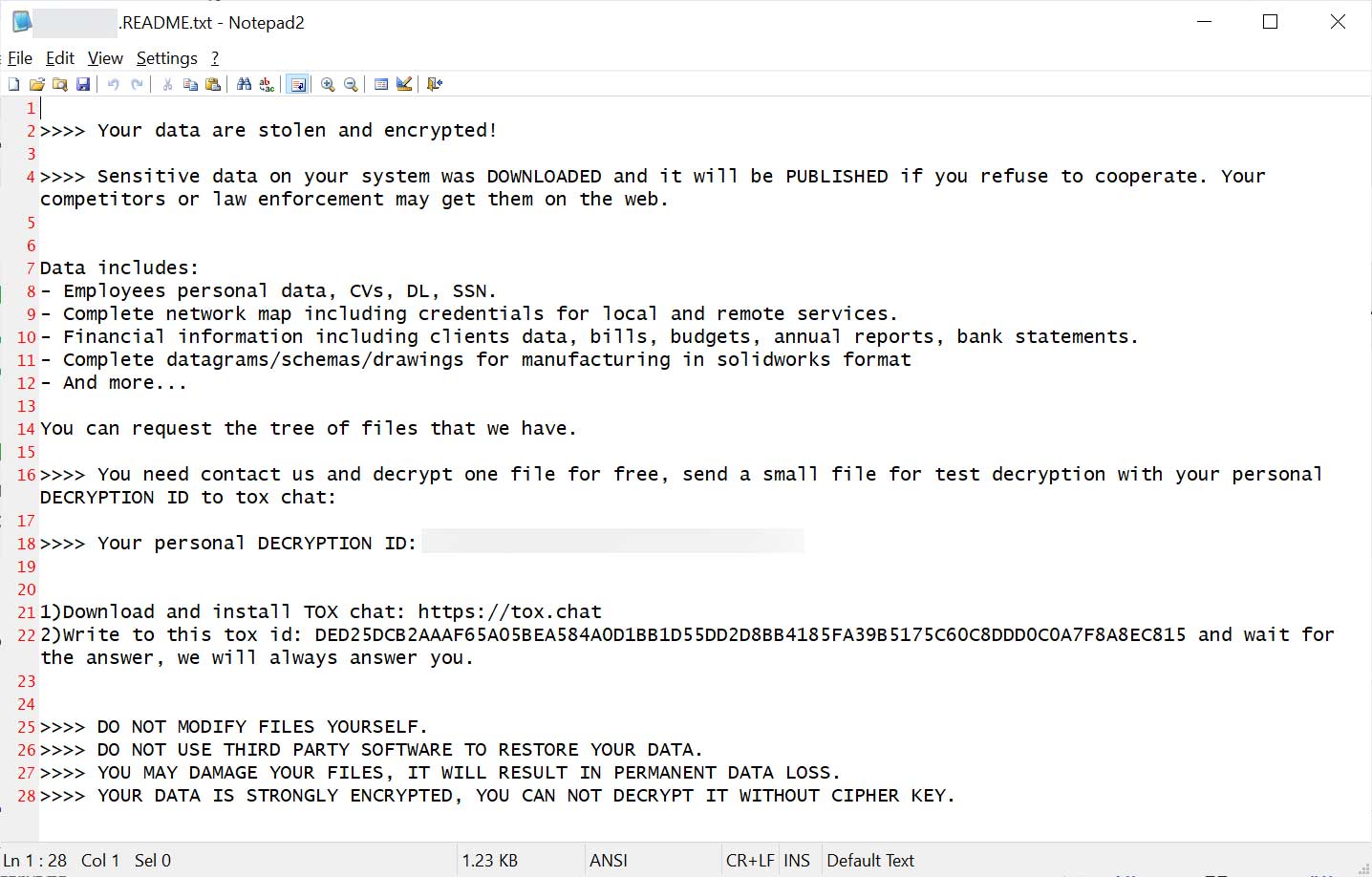
After the encryption course of, rescue notes are decreased within the sufferer’s system. Then a customized wiper is carried out known as ‘Tallblack’ to remove all of the traces of the ransomware executable to hinder the forensic evaluation.
Supply: Forecout
Lockbit’s SuperBlack Hyperlink
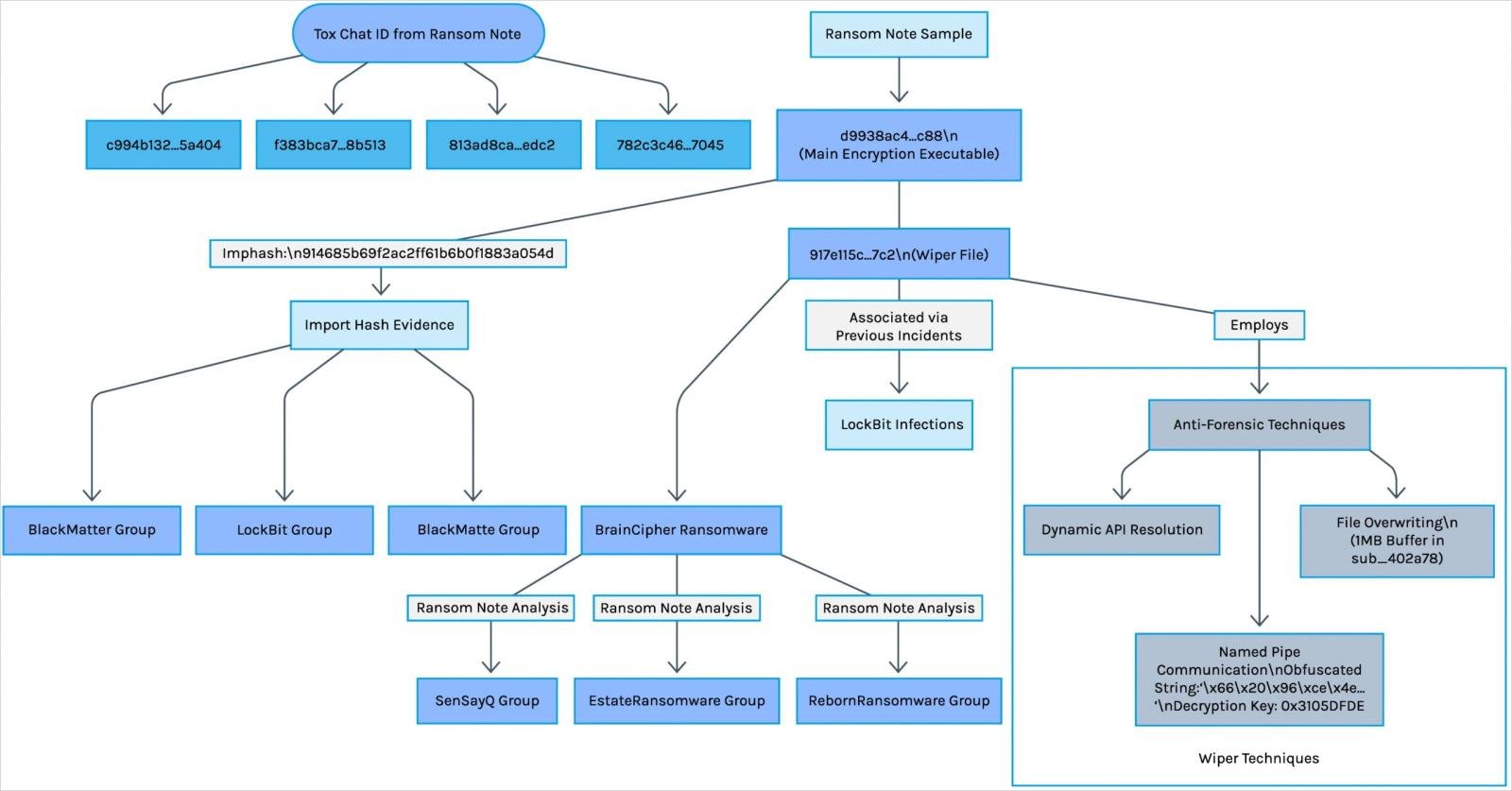
Foresout has discovered ample proof that signifies robust hyperlinks between the Ransomware Superblack and Ransomware Lockbit operation, though the primary appears to behave independently.
The primary component is that the superblack encryption (Virusta) It’s based mostly on the Builder filtered 3.0 by Lockbit, with an similar payload construction and encryption strategies, however all unique model stripes.
Supply: Forecout
Secondly, SuperBlack’s rescue notice contains an identification of tox chat linked to Lockbit’s operations, suggesting that Mora_001 is a former Lockbit affiliate or a former member of his primary staff that manages rescue funds and negotiations.
The third component that implies a hyperlink is the intensive IP tackle superimposed with earlier Lockbit operations. As well as, Wallblack has additionally been taken benefit of by Braincipher ransomware, the SENSAYQ EMBERSOMWARE and ransomware, all linked to Lockbit.
Foresout has shared an in depth checklist of compromise indicators (IOC) linked to superblack ransomware assaults on the backside of its report.


