Though Oracle denies a violation of its Oracle Cloud Federated SSO login servers and the theft of account knowledge for six million individuals, Bleepingcompter has confirmed with a number of firms that the related knowledge samples shared by the risk actor are legitimate.
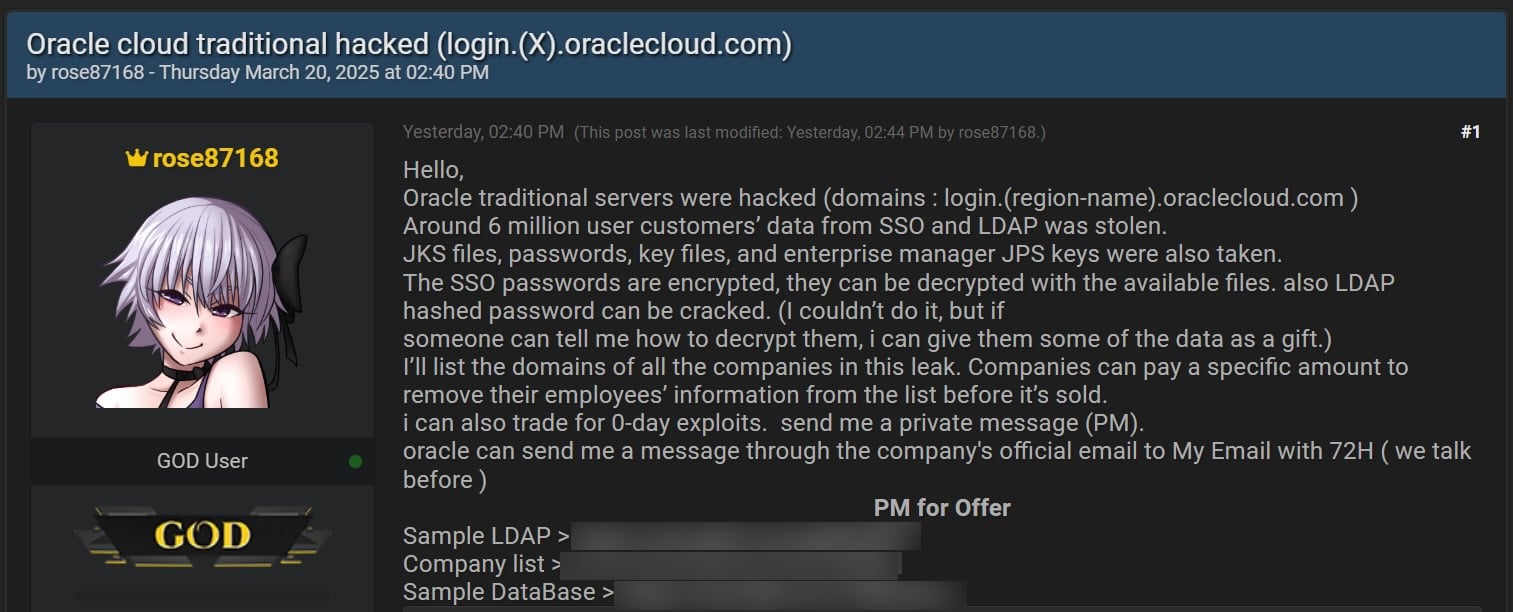
Final week, an individual named ‘Rose87168’ stated Oracle Cloud Servers Rallados and commenced promoting the supposed authentication knowledge and encrypted passwords of 6 million customers. The risk actor additionally stated that the stolen passwords of SSO and LDAP may decipher utilizing the knowledge within the stolen information and supplied to share among the knowledge with anybody who may help recuperate them.
The risk actor revealed a number of textual content information consisting of a database, LDAP knowledge and a listing of 140,621 domains of firms that have been supposedly affected by the violation. It needs to be famous that among the firm’s domains appear proof, and there are a number of domains per firm.
Supply: Bleepingcomter
Along with the info, Rose87168 shared a Archive.org URL With Bleepingcomputer for a textual content file lodged on the server “login.us2.oraclecloud.com” containing its e mail handle. This file signifies that the risk actor may create information on the Oracle server, indicating an actual violation.
Nevertheless, Oracle has denied that he suffered a rape of Oracle Cloud and has refused to reply any further questions in regards to the incident.
“There has not been a rape of Oracle Cloud. The revealed credentials usually are not for Oracle Cloud. No Oracle Cloud consumer skilled a rape or misplaced knowledge,” the corporate advised Bleepingcomter final Friday.
Nevertheless, this denial contradicts the Bleepingcomter findings, which obtained further samples from the leaked knowledge from the risk actor and contacted the related firms.
Representatives of those firms, all who agreed to substantiate the info below the promise of anonymity, confirmed the authenticity of the knowledge. The businesses declared that the related LDAP visualization names, the e-mail addresses, the stack names and different identification info have been right and belonged to them.
The risk actor additionally shared emails with Bleepingcomter, claiming to be a part of an change between them and Oracle.
An e mail exhibits the risk actor who contacted the Oracle safety e mail ([email protected]) to report that the servers pirate.
“I’ve deepened in its cloud board infrastructure and I discovered an enormous vulnerability that has given me full entry to details about 6 million customers,” reads e mail seen by Bleepingcomuter.
One other thread shared with Bleepingcomputer exhibits an change between the risk actor and somebody who makes use of a protonmail e mail handle that claims to be from Oracle. Bleepingcomuter has written the e-mail handle of this different individual, since we couldn’t confirm their identification or the veracity of the e-mail thread.
On this e mail change, the risk actor says that somebody from Oracle utilizing an e mail handle @proton.
The Cloudsek cybersecurity agency additionally has discovered a Archive.org URL Displaying that the server “login.us2.oraclecloud.com” was executing Oracle Fusion Middleware 11G as of February 17, 2025. Oracle since then has dominated out this server after information of the alleged violation was reported.
This model of the software program was affected by a tracked vulnerability as CVE-2021-35587 That allowed non -authenticated attackers to compromise Oracle Entry Supervisor. The risk actor stated that this vulnerability was used within the alleged violation of Oracle servers.
Bleepingcomuter has despatched an e mail to Oracle on quite a few events about this info, however has not obtained any response.


