Pc pirates are launching assaults in opposition to Palo Alto Pan -os Firewalls exploiting a just lately fastened vulnerability (CVE-2025-0108) that enables authentication to be neglected.
The safety drawback acquired a excessive severity rating and impacts the PAN-OS administration internet interface and permits an attacker not authenticated on the community to keep away from authentication and invoke sure PHP scripts, which may compromise integrity and confidentiality.
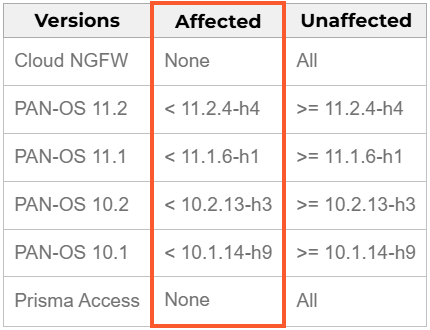
In Safety Bulletin On February 12, Palo Alto Networks urges directors to replace the Firewalls to the variations beneath to handle the issue:
- 11.2.4-H4 or posterior
- 11.1.6-H1 or later
- 10.2.13-H3 or posterior
- 10.1.14-H9 or posterior
PAN-OS 11.0 can be affected, however the product reached the tip of life (EOL) and Palo Alto Networks doesn’t plan to launch any resolution for him. Due to this, customers are strongly really useful to replace to a suitable model.
Supply: Palo Alto Networks
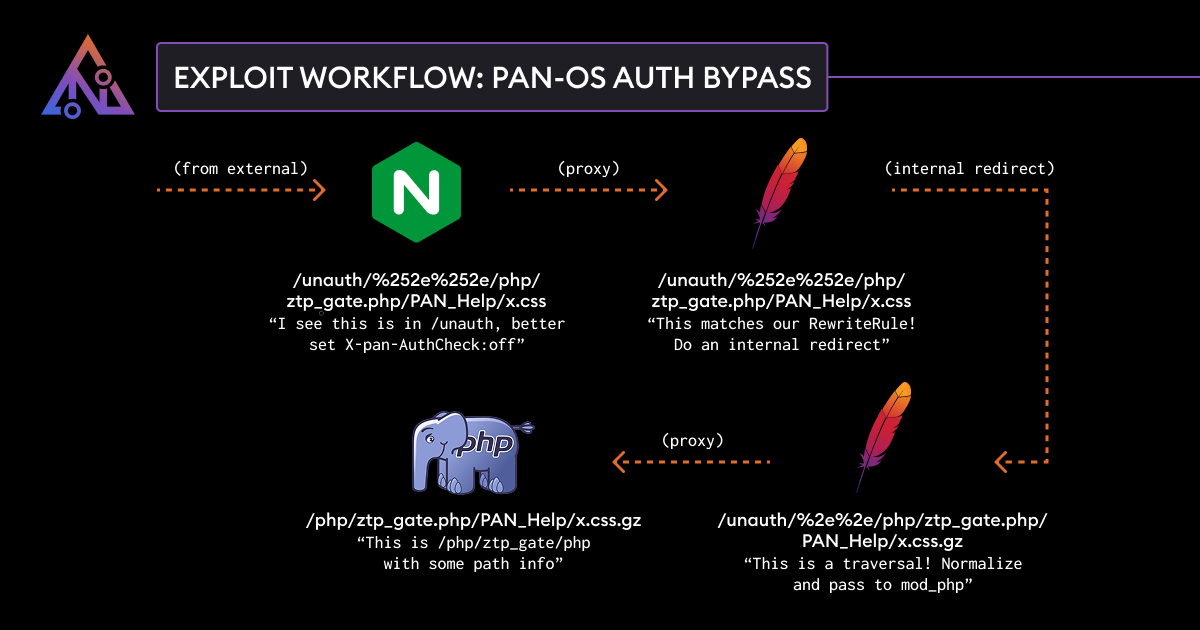
The vulnerability was found and knowledgeable to Palo Alto networks by Assetnote safety researchers. Additionally they revealed an article with Full exploitation particulars When the patch was launched.
The researchers demonstrated how the failure could possibly be used to extract confidential information from the system, get better doubtlessly manipulate firewall configurations or manipulate sure configurations inside PAN-OS.
The exploit takes benefit of a confusion route between Nginx and Apache in Pan -os that enables the authentication to go.
Attackers with entry to the community to the administration interface can benefit from this to gather intelligence for extra assaults or weaken safety defenses by modifying accessible configuration.
Supply: Assetnote
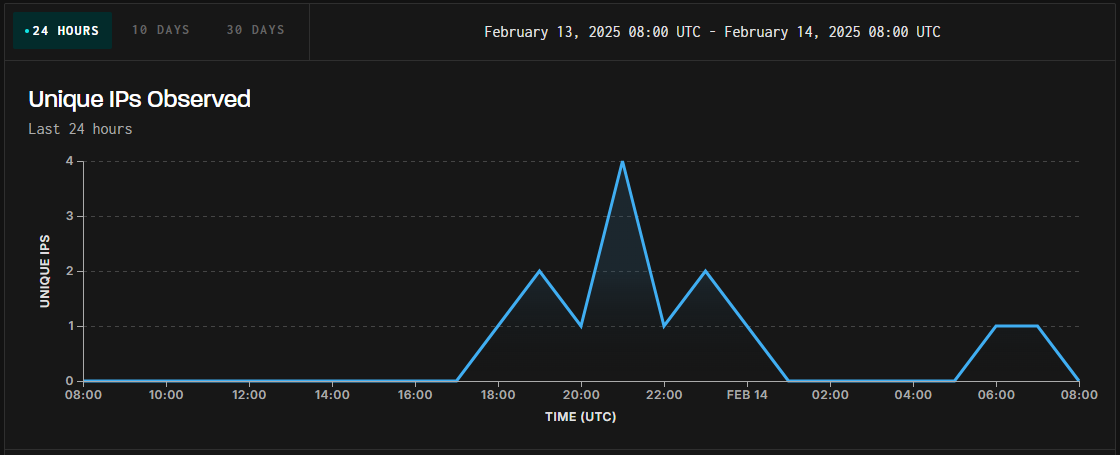
Greynoise registered menace monitoring platform exploitation makes an attempt aimed on the Firewalls Pan -os with out blinking.
The assaults started on February 13 at 5:00 p.m. UTC, and appear to originate in a number of IP instructions, which can point out the exploitation efforts of various menace actors.
Supply: Graynoise
Concerning the exhibition of weak units on-line, Macnica researcher Yutaka Sejiyama informed Bleepingcom that there are at present greater than 4,400 pan -os units that expose her on-line administration interface.
To defend in opposition to the present exploitation exercise, which, bearing in mind that PIC is public, it is extremely more likely to culminate within the following days, it is strongly recommended to use the accessible patches and prohibit entry to Firewall administration interfaces.

