Most corporations have robust exterior safety, for instance, blocking all entry to manufacturing property via a firewall and requiring a VPN to realize “inner” entry to manufacturing environments. Nevertheless, as soon as related to the VPN, inner programs are sometimes very poorly protected and there’s little to no authentication and authorization for inner instruments and providers.
Two frequent inner safety threats are compromised worker laptops and provide chain assaults. In these situations, the attacker operates behind the firewall, typically with unrestricted community entry.
Providers with an online UI might be protected utilizing an software load balancer, for instance a AWS ALB with OIDCHowever how do you defend entry to instruments primarily based on the command line interface (CLI)? Requiring a username and password for every CLI invocation makes them cumbersome to make use of, and storing credentials on the system leaves them open in case the pc they reside on is compromised.
The command line
Most inner instruments have a CLI to handle the providers used inside the firm and plenty of are poorly protected. What’s one of the best ways to authorize CLI? And the way can authorization be linked to the corporate’s SSO?
One possibility is to implement Hashicorp Vault, however that requires numerous setup and upkeep, so except you will have a workforce to function it, Vault might not be a great possibility.
An alternative choice is granting OAuth2 machine authorization (RFC8628), which is what this weblog put up will present you the way to use.
OAuth 2.0 Gadget Authorization Grant is designed for Web-connected gadgets that lack a browser to carry out consumer agent-based authorization or which have enter restricted to the purpose of requiring the consumer to enter textual content to authenticate throughout the circulation. authorization. impractical. Permits OAuth shoppers on such gadgets (akin to good TVs, media consoles, digital frames, and printers) to acquire consumer authorization to entry protected sources by utilizing a consumer agent on a separate machine.
Should you’ve ever used the AWS CLI with Single SignOn, this is what it does.
OAuth2 machine circulation
The machine authorization circulation comprises two completely different paths; one happens on the machine requesting authorization (the CLI) and the opposite happens in a browser. The browser circulation path, wherein a tool code is certain to the session within the browser, happens as a parallel path half within the machine circulation path.
OAuth Gadget Circulation Implementation
Now we are going to see what the above sequence diagram appears to be like like when applied.
The interior CLI device in Rockset is named rsctl and it’s written in go. Step one is to start out the machine circulation to acquire a JWT entry token.
$ rsctl login
Trying to routinely open the SSO authorization web page in your default browser.
If the browser doesn't open otherwise you want to use a distinct machine to authorize this request, open the next URL:
https://rockset.auth0.com/activate?user_code=BBLF-JCWB
Then enter the code:
BBLF-JCWB
Efficiently logged in!
In case you are utilizing the CLI after logging in to a different laptop, for instance ssh:ing to a Linux server, and you utilize macOS, you possibly can configure iTerm to routinely open the hyperlink utilizing a “Run command” set off.
The web page the hyperlink takes you to appears to be like like this:
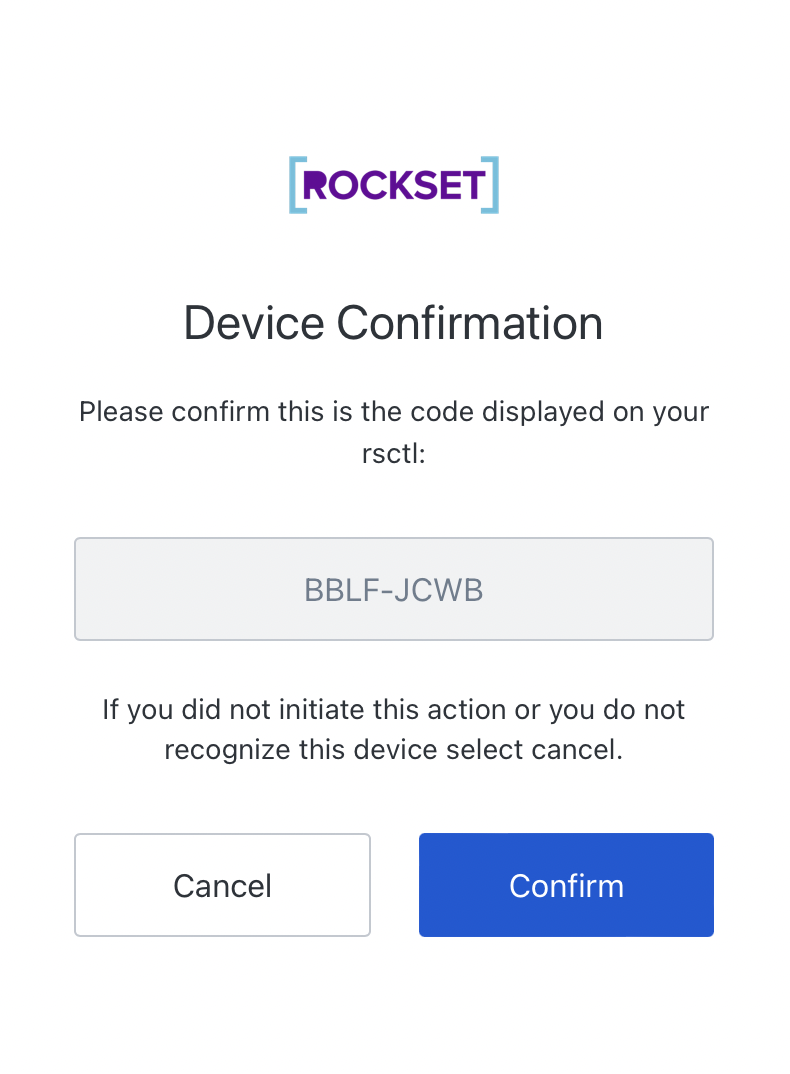
After you have confirmed that the “consumer code” is appropriate (matches what the CLI exhibits) and click on “Affirm”, it is going to take you thru the traditional OAuth2 login process (which in our case requires a username, password and {hardware}). symbolic).
As soon as the authentication is accomplished, you’ll be redirected and offered with a dialog field just like the one proven under, and you may shut the browser window.
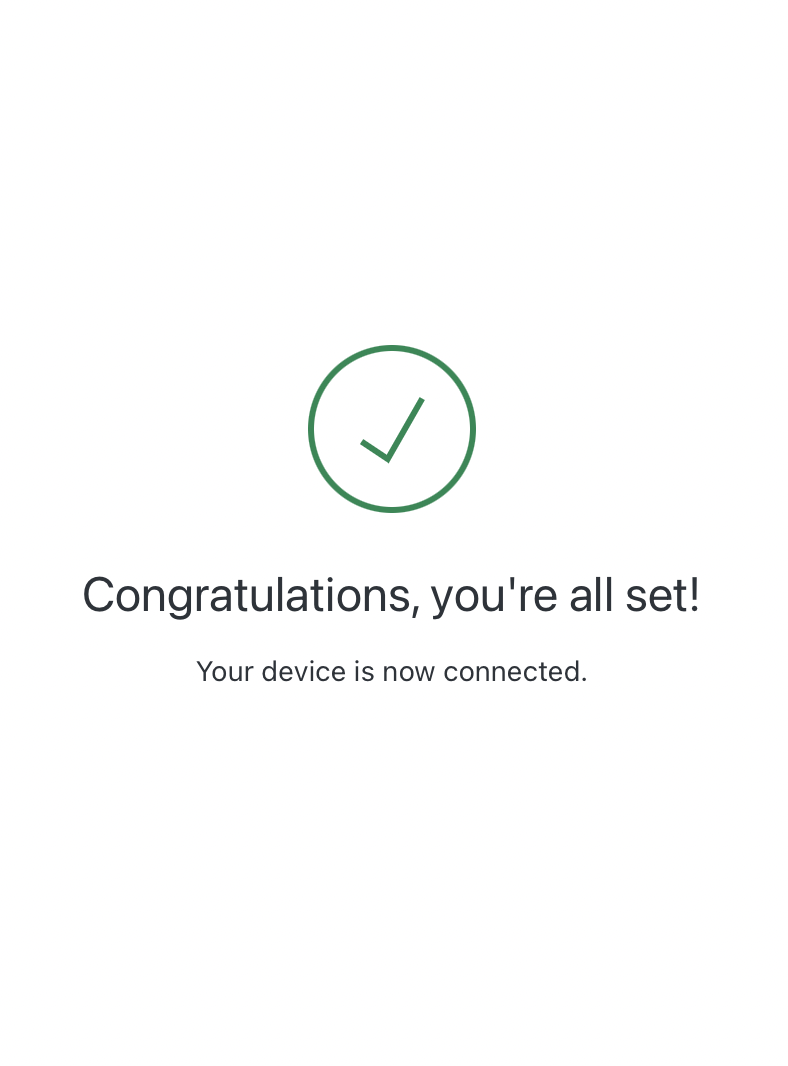
The CLI has now obtained a jwt entry token which is legitimate for numerous hours and is used to authenticate via inner providers. The token might be cached to disk and reused between CLI invocations throughout its lifetime.
Once you situation a brand new rsctl command, it is going to learn the cached entry token from disk and use it to authenticate with the inner APIs.
underneath the hood
We have now applied and opened a go module to carry out the machine authorization circulation (github.com/rockset/device-authorization). Helps each Auth0 and Okta as OAuth suppliers.
Pattern code
The next code is accessible within the instance listing within the git repository.
Embedded content material: https://gist.github.com/pmenglund/5ed2708cdb88b6a6982258aed59a0899
We now have a JWT token, which can be utilized to authenticate REST calls by setting the Authorization header to Bearer:
Embedded content material: https://gist.github.com/pmenglund/b2ac7bb15ce25755a69573f5a063cb14
It’s now as much as the receiving finish to validate the bearer token, which might be executed utilizing a AWS ALB with OIDC authentication or a Vendor Particular API from the API server.
Offline validation
An alternative choice for entry token validation is “offline validation”. In offline validation, the API server obtains the general public key used to signal the JWT token from the supplier (and caches the general public key) and performs validation on the API server, as a substitute of constructing a validation request to the supplier. .
Residual danger
One factor this does not defend in opposition to is an attacker with a foothold on the pc operating the CLI. They’ll merely wait till the consumer has accomplished authentication after which they’ll act because the consumer at some point of the entry token.
To mitigate this danger, you possibly can require a one-time password (OTP), for instance Yubikey, every time the consumer performs a privileged motion.
$ rsctl delete useful resource foobar
please enter yubikey OTP: ccccccvfbbcddjtuehgnfrbtublkuufbgeebklrubkhf
useful resource foobar deleted
Last ideas
On this weblog, we present how we create and open a go module to safe the command line interface (CLI) utilizing an OAuth2 machine authorization circulation that helps Auth0 and Okta SSO suppliers. You may add this go module to your inner instruments and scale back inner safety threats.

