Cybercriminals are abusing Microsoft’s confidence agency platform to signal code code malware executables with three -day length certificates.
Menace actors have lengthy sought code signing certificates, since they can be utilized to signal malware in order that they seem like a reliable firm.
The signed malware additionally has the benefit of avoiding security filters that the executable executables would usually block, or at the least deal with them with much less suspicions.
The Holy Grail for menace actors is to acquire prolonged validation code signing certificates (EV), since they robotically receive larger confidence from many cyber safety packages because of the most rigorous verification course of. Much more essential, it’s believed that EV certificates receive an impulse of status on the sensible display screen, which helps keep away from alerts that might usually be displayed for unknown recordsdata.
Nonetheless, EV code certificates might be tough to acquire, which requires them to be stolen from different firms or menace actors to determine false companies and spend 1000’s of {dollars} to purchase one. As well as, as soon as the certificates is utilized in a malware marketing campaign, it’s typically revoked, which makes it ineffective for future assaults.
Abuse Microsoft’s belief agency service
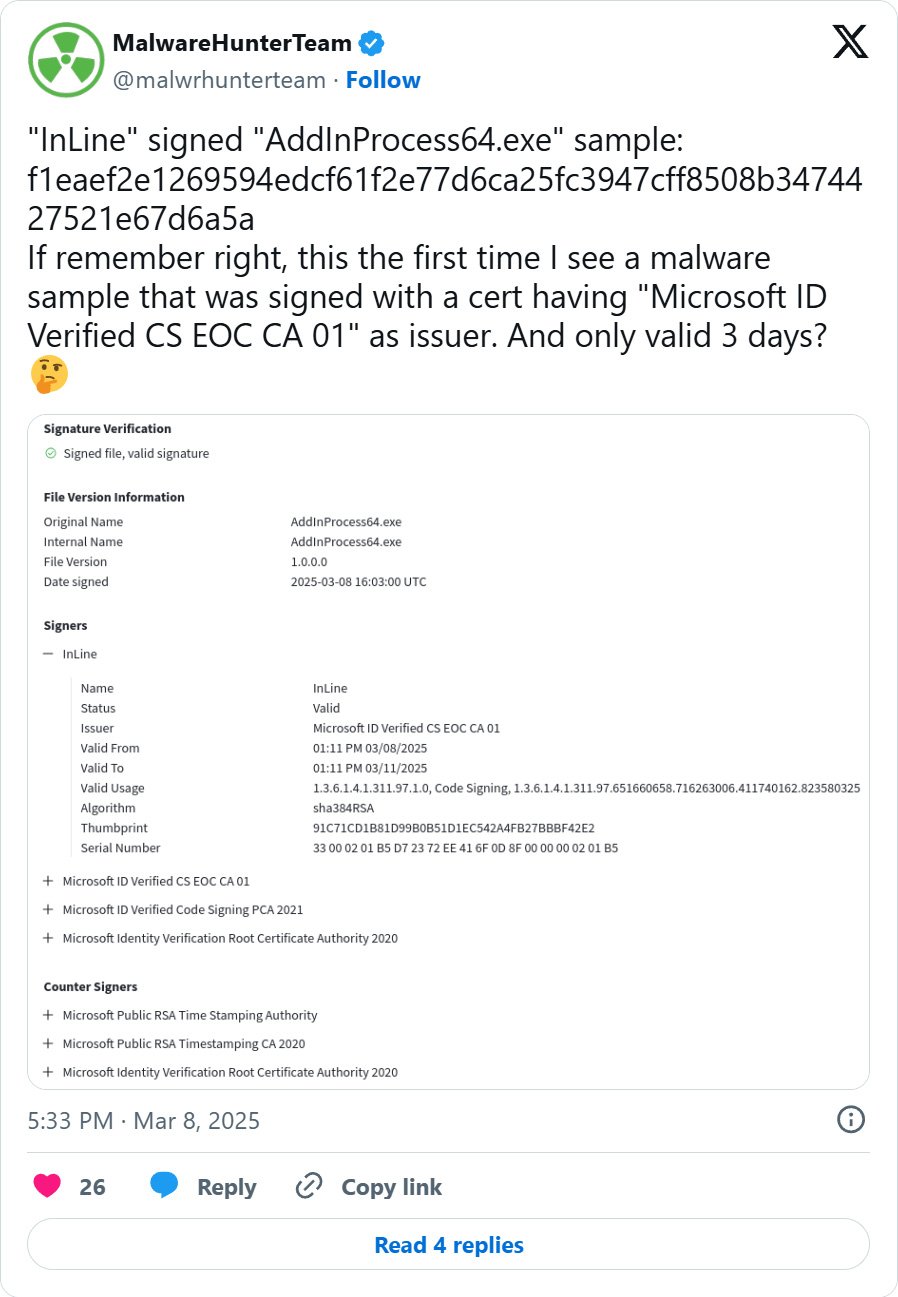
Just lately, cybersecurity researchers have seen menace actors utilizing the Microsoft’s belief agency service To signal your malware with three -day length code agency certificates.
These malware samples are signed by “Microsoft ID verified CS EOC CA 01” and the certificates is barely legitimate for 3 days. Whereas the certificates expires three days after being issued, it is very important remember that the executables signed with it’s going to nonetheless be thought-about legitimate till the issuer revokes the certificates.
Since then, different researchers and BleepingCompter have discovered many different samples utilized in present malware campaigns, together with these utilized in a Loopy evil methods Cryptoft marketing campaign (Virusta) and Lumma Stealer (Virusta) Campaigns.
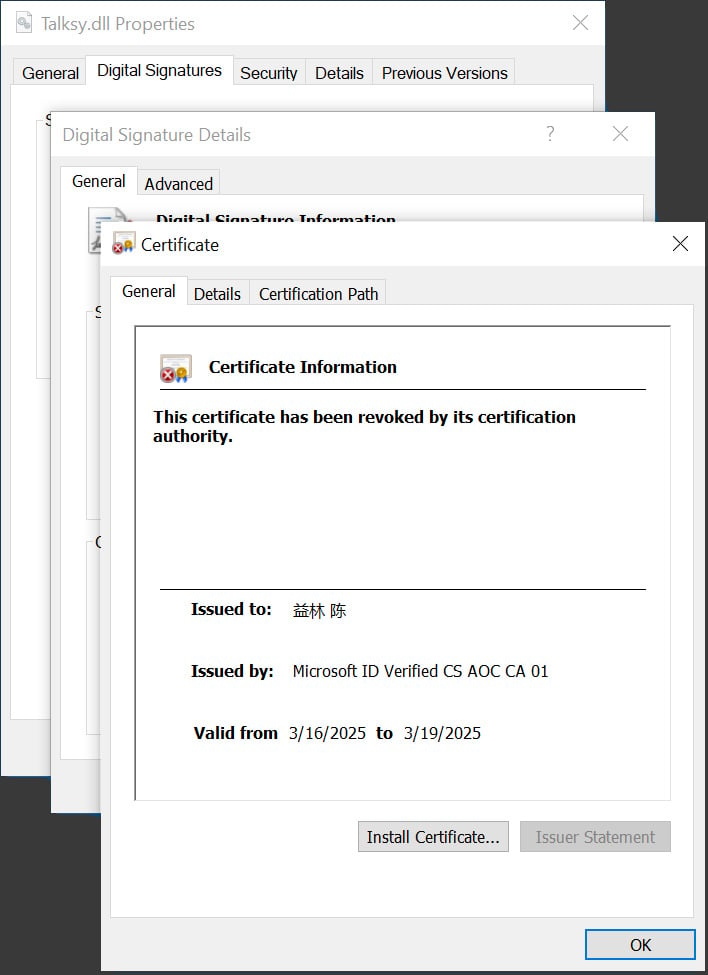
Supply: Bleepingcomter
He Microsoft’s belief agency service Launched in 2024 and is a cloud -based service that enables builders to have their packages simply signed by Microsoft.
“The belief agency is an entire code signature service with an intuitive expertise for builders and IT professionals, backed by a certification authority administered by Microsoft,” reads Microsoft advert For service.
“The service admits private and non-private confidence agency eventualities and features a time model service.”
The platform has a month-to-month subscription service of $ 9.99 designed to facilitate builders to signal their executables, whereas providing extra safety.
This enhance in safety is achieved through the use of quick -term certificates that may be simply revoked in case of abuse and by no means concern certificates on to builders, stopping them from being stolen in case of violation.
Microsoft additionally says that the certificates issued by means of the trusted agency service present an impulse for sensible display screen status much like the executables signed by their service.
“A dependable signature agency ensures that its utility is relied on to offer base status on the sensible display screen, confidence in Home windows consumer mode and signature validation integrity verification,” reads steadily requested questions on the positioning of confidence signature.
To guard in opposition to abuse, Microsoft is It presently solely permits Certificates can be issued underneath the title of an organization if they’ve been in enterprise for 3 years.
Nonetheless, folks can register and be authorized extra simply in the event that they agree with the certificates issued underneath their title.
An easier path
A cybersecurity researcher and developer often called ‘Squitlydoo’, who has been monitoring malware campaigns that abuse certificates for years, advised Bleepingcomter that they imagine that menace actors are altering to the Microsoft service for comfort.
“I believe there are some causes for the change. For a very long time, using EV certificates has been the usual, however Microsoft has introduced modifications in EV certificates,” Squidodoo advised Bleepingcomuter.
“Nonetheless, modifications in EV certificates are actually not clear to anybody: not certificates suppliers, not attackers. Nonetheless, on account of these potential modifications and lack of readability, simply having a code signature certificates might be sufficient for the wants of the attackers.”
“On this sense, the verification course of for Microsoft certificates is considerably simpler than the verification course of for EV certificates: on account of ambiguity on EV certificates, it is sensible to make use of Microsoft certificates.”
Bleepingcomputer contacted Microsoft about abuse and advised him that the corporate makes use of menace intelligence monitoring to seek out and revoke certificates as they’re discovered.
“We use energetic intelligence monitoring of threats to always seek for any improper use or abuse of our signature service,” Microsoft advised Bleepingcomuter.
“Once we detect threats, we instantly mitigate with actions such because the revocation of broad certificates and the suspension of the account. The malware samples they shared are detected by our antimalware merchandise and we now have already taken measures to revoke the certificates and keep away from the abuse of account extra.”