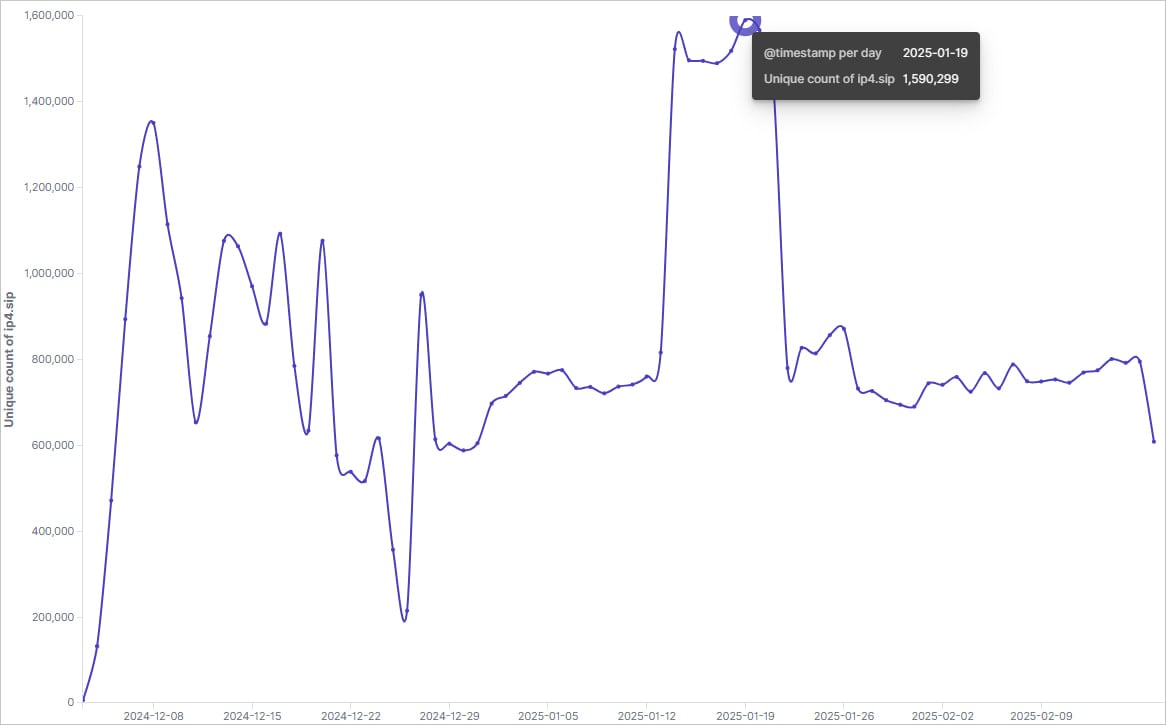
A brand new variant of the Malware Botnet VO1D has grown to 1,590,299 Android TV units contaminated in 226 international locations, recruiting units as a part of proxy servers nameless networks.
That is in accordance with a XLAB analysisThat he has been monitoring the brand new marketing campaign since final November, informing that Botnet reached its most level on January 14, 2025 and presently has 800,000 lively bots.
In September 2024, Dr. Internet antivirus researchers discovered 1.3 million units In 200 international locations compromised by VO1D malware via an unknown an infection vector.
The latest XLAB report signifies that the brand new model of the VO1D botnet continues its operations on a bigger scale, not deterred by the earlier exhibition.
As well as, the researchers underline that the botnet has developed with superior encryption (RSA + XXTEA Personalised), DGA resistant infrastructure and improved stealth capabilities.
Supply: Xlab
Mass botnet measurement
The VO1D botnet is without doubt one of the best seen in recent times, surpassing BigpanziMirai’s unique operation, and the botnet chargeable for a registration breakdown 5.6 TBPS DDOS assault Managed by Cloudflare final yr.
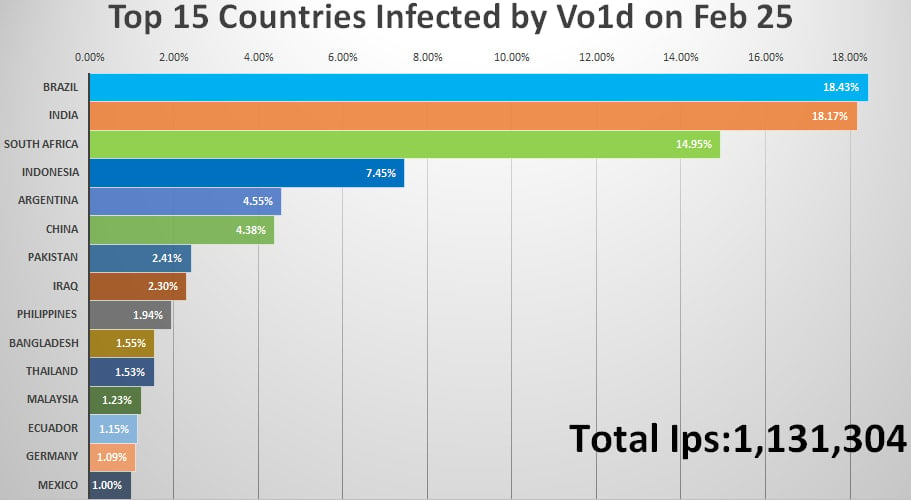
As of February 2025, virtually 25percentof infections affect Brazilian customers, adopted by units in South Africa (13.6%), Indonesia (10.5%), Argentina (5.3%), Thailand (3.4%) and China (3.1%).
Researchers report that the botnet has had notable an infection overcomes, corresponding to from 3,900 to 217,000 bots in India in simply three days.
Longest fluctuations recommend that Botnet operators could be “renting” units corresponding to proxy servers, that are generally used to carry out criminality or booty.
“We speculate that the phenomenon of” speedy overthensions adopted by an acute lower “could be attributed to the VO1D lease its botnet infrastructure in particular areas to different teams. That is how this” rental rental cycle “may work:
Lease section:
In the beginning of a lease, the bots deviate from the primary VO1D community to serve the lessee operations. This deviation causes a sudden fall within the VO1D infections depend because the bots are quickly eradicated from their lively group.
Return section:
As soon as the lease interval ends, the bots bind to the VO1D community. This reintegration results in a speedy enhance in infections counts because the bots turn out to be lively once more underneath VO1D management.
This cyclic mechanism of “lease and return” may clarify the fluctuations noticed within the VO1D scale at particular time factors. “
❖ Xlab
The size of its command and management infrastructure (C2) can also be spectacular, with the operation utilizing 32 seeds of area era (DGA) to supply greater than 21,000 C2 domains.
C2 communication is protected by a 2048 -bit RSA key, so even when researchers determine and report a C2 area, they can not difficulty instructions to the bots.
Supply: Xlab
Vo1D capacities
The VO1D botnet is a multipurpose cybercrime crime instrument that converts the units dedicated to Proxy servers to facilitate unlawful operations.
Contaminated units transmit malicious site visitors for cybercriminals, hiding the origin of their exercise and are blended with residential networks. This additionally helps the menace that the actors don’t overlook regional restrictions, safety filtering and different protections.
One other VO1D operate is promoting fraud, faux person interactions simulating clicks on ads or views on video platforms to generate earnings for fraudulent advertisers.
Malware has particular equipment that automate promoting interactions and simulate navigation conduct just like people, in addition to Mzmess SDK, which distributes fraud duties to totally different bots.
Because the an infection chain remains to be unknown, it is suggested that Android TV customers observe a holistic safety method to mitigate the VO1D menace.
Step one is to purchase good fame suppliers and dependable resellers to reduce the likelihood that the malware shall be preloaded from the manufacturing unit or whereas in transit.
Secondly, it’s essential to put in firmware and safety updates that shut the areas that can be utilized for distant infections.
Third, customers ought to keep away from downloading purposes exterior Google Play or third -party firmware pictures that promise prolonged and “unlocked performance.”
Android TV units will need to have their distant entry features disabled if not vital, whereas being misplaced when it’s not used can also be an efficient technique.
Finally, IoT units should be remoted from beneficial units that include confidential knowledge on the community stage.

